In July 2025, security researchers uncovered CVE-2025-49596, a critical remote code execution vulnerability scoring 9.4 on the CVSS scale in Anthropic’s MCP Inspector. This widely-trusted developer tool, with over 38,000 weekly downloads and 4,000+ GitHub stars, had become a silent gateway to complete system compromise. What made this vulnerability particularly dangerous was its simplicity: attackers needed only to lure victims to a malicious website. No phishing emails, no suspicious downloads, no additional clicks required.
CVE-2025-49596 represents an evolution in attack methodology, targeting the trust relationship between development tools and local systems. The vulnerability exploited a critical oversight in how MCP Inspector handled security at the intersection of web browsing and local services, a boundary that developers increasingly assume is safe but which modern browser behavior has fundamentally blurred.
Anatomy of the Vulnerability
MCP Inspector comprises two essential components working in tandem. The MCP Inspector Client provides a React-based web interface for monitoring MCP server communications, while the MCP Proxy acts as a Node.js protocol bridge accepting stdio commands. The vulnerability originated in the proxy’s fundamental design flaw: it accepted arbitrary stdio commands from any source without authentication or origin validation.
When developers executed the recommended installation command both components would spin up automatically with the proxy binding to all network interfaces (0.0.0.0) by default. This created an attack surface that was both wide and easily discoverable, operating under the assumption that all requests originated from legitimate local development activities.
The exploitation technique leverages a subtle but critical browser behavior: Chrome and Firefox treat the IP address 0.0.0.0 as functionally equivalent to localhost. Combined with MCP Inspector’s permissive CORS configuration allowing all origins, this created the perfect storm. An attacker crafts a malicious webpage with JavaScript designed to communicate with the victim’s local MCP Inspector instance. When the victim visits the page, their browser dispatches cross-origin requests to the local proxy, passes the CORS preflight check, and executes the attacker’s commands, achieving arbitrary code execution without any warning or interaction.
Measuring the Blast Radius
The vulnerability’s reach extended far beyond individual developer workstations. Major technology companies including Microsoft and Google had integrated MCP-related technologies into their AI and cloud services, exposing their development teams to potential compromise. Open-source projects that adopted MCP as a standard protocol component unwittingly recommended vulnerable tooling in their official documentation.
Internet-wide scanning revealed over 560 exposed MCP Inspector instances, with the majority concentrated in the United States and China, reflecting these regions’ leadership in AI development. Organizations in financial services, energy, education, and healthcare represented particularly high-value targets as these sectors raced to integrate AI capabilities. The vulnerability didn’t just threaten code and credentials; it endangered entire development pipelines, intellectual property, and the supply chain security of AI applications under active development.
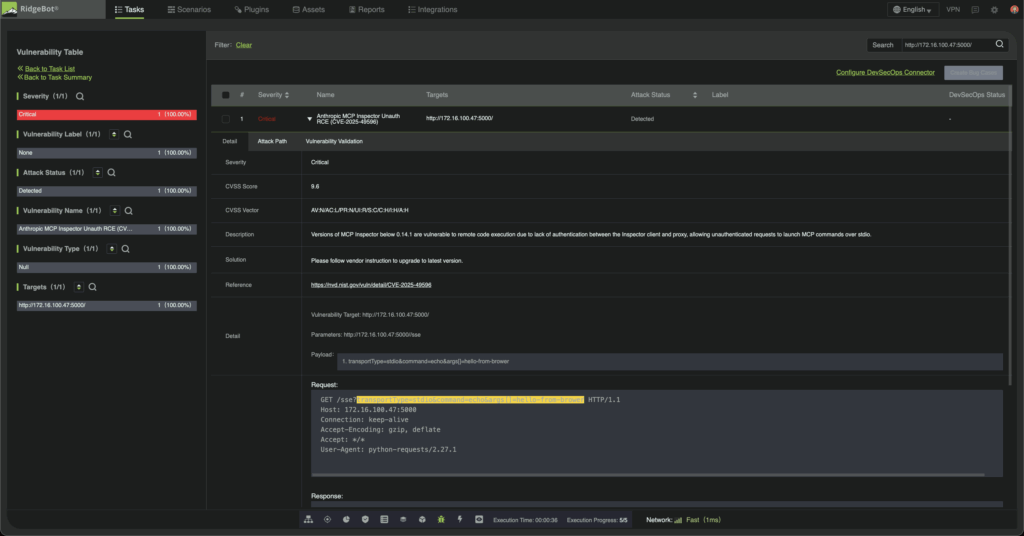
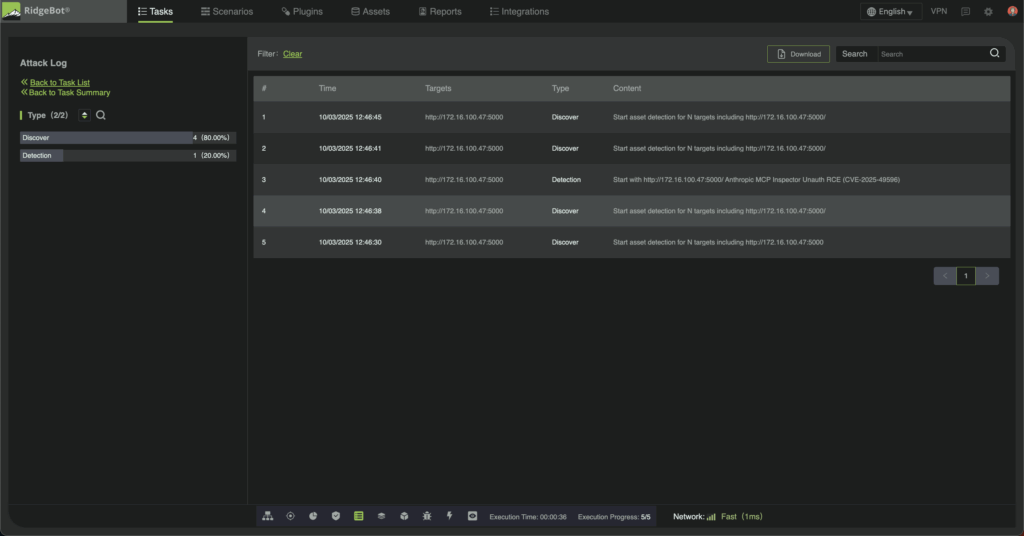
CVE-2025-49596 exposes a critical reality: the assumption that localhost is safe no longer holds. In an era where browser-based attacks can bridge public internet and local services, even trusted AI development tools become potential attack vectors.
RidgeBot addresses this threat with automated detection that compresses security validation from weeks to hours. Specialized plugins simulate the complete attack chain, reconnaissance through exploitation, identifying vulnerable MCP Inspector instances and providing detailed evidence before threat actors can weaponize them.
This vulnerability serves as a stark reminder: your AI development tools are only as secure as their weakest assumption. RidgeBot’s rapid response capabilities, backed by threat intelligence and AI-driven decision-making, ensure organizations can identify and remediate emerging vulnerabilities before they become breaches, delivering continuous protection for modern enterprises where AI development and production systems increasingly converge.
