Background
Gogs Path Traversal and Remote Code Execution is a critical vulnerability affecting the self-hosted Git service Gogs (Go Git Service) versions 0.13.3 and earlier. First observed in active exploitation in mid-2025, the flaw was quickly weaponized, compromising over 700 publicly exposed instances out of roughly 1,400 observed.
Due to confirmed in-the-wild attacks, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the vulnerability to its Known Exploited Vulnerabilities catalog, requiring federal agencies to remediate by February 2, 2026, and strongly recommending that private organizations take immediate action.
Root Cause
The issue stems from improper symbolic link handling in the Gogs PutContents API. While the API validates filenames and repository paths, it does not verify whether the resolved target is a symbolic link pointing outside the repository directory.
This symlink blind spot allows write operations to escape repository boundaries. When the operating system follows the symlink, attackers can overwrite arbitrary files on the host. The vulnerability bypasses a previous fix for a related path traversal vulnearbility (CVE-2024-55947)), which addressed direct directory escapes but did not account for symbolic links.
Attack Chain
Exploitation requires only authenticated access and follows a straightforward sequence:
- An attacker registers a new account (if open registration is enabled) or logs in using valid credentials.
- Once authenticated, the attacker creates a repository and commits a malicious symbolic link that points to a sensitive file outside the repository, such as .git/config.
- The attacker then uses the PutContents API to write content through the symlinked path.
- Although Gogs validates the filename, it does not resolve the symbolic link, allowing the operating system to overwrite the external target file.
- Malicious configuration options are injected into .git/config.
- When Git operations are subsequently triggered, arbitrary commands are executed on the server.
- A reverse shell is established, granting the attacker full interactive access to the system.
This chain allows an authenticated user to escape repository isolation and achieve full remote code execution on the Gogs host.
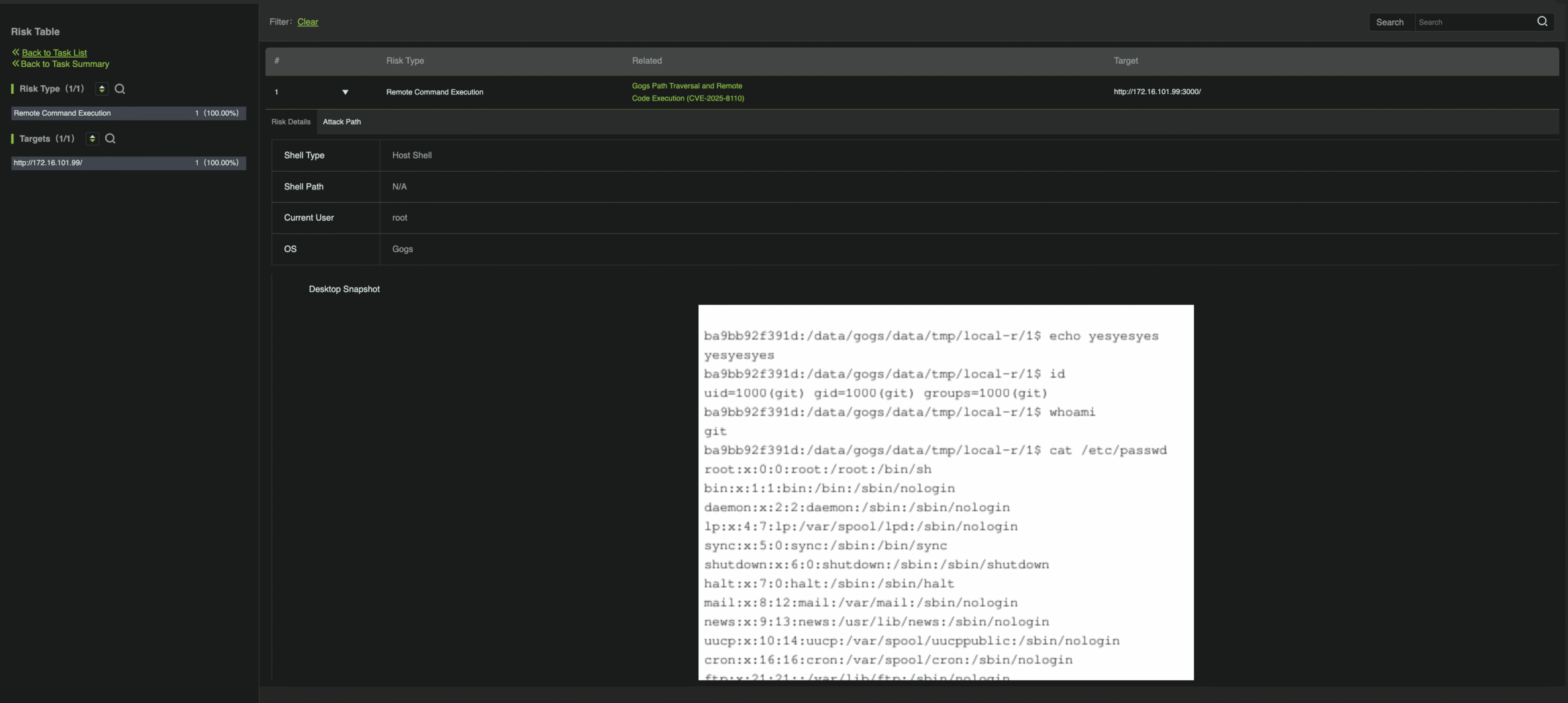
Detection and Exploitation on RidgeBot
The screenshot below demonstrates RidgeBot detecting the vulnerable behavior and confirming successful exploitation. The remote code execution proof is shown as a reverse shell session from the Gogs server to the attacker’s system. A reverse shell indicates full command execution capability, meaning the attacker can run arbitrary commands and fully control the compromised host.
Remediation
Organizations should immediately reduce exposure by limiting internet access, disabling open registration, and restricting API usage to trusted users. While awaiting a permanent fix, monitoring symbolic link creation, unexpected Git configuration changes, and abnormal command execution is essential.
Because this vulnerability is actively exploited, passive scanning is not enough. RidgeBot provides active validation, safely confirming exploitability, including remote code execution paths. This allows security teams to prioritize patching and protect exposed environments before attackers can take advantage of the flaw.
