Ridge Security’s Immediate Response
CISA has recently added two critical vulnerabilities, CVE-2025-61882 and CVE-2025-61884, to its Known Exploited Vulnerabilities (KEV) Catalog, both affecting Oracle E-Business Suite. CVE-2025-61882 is a critical, unauthenticated vulnerability in the BI Publisher Integration component of Oracle Concurrent Processing that has been actively exploited. CVE-2025-61884 is a high-severity information disclosure vulnerability in the Runtime UI component of Oracle Configurator, which has also been patched by Oracle.
Together, these vulnerabilities create a perfect storm: CVE-2025-61882 (CVSS 9.8) enables unauthenticated remote code execution and has been weaponized by the Clop ransomware group since August 2025, while CVE-2025-61884 (CVSS 7.5) allows unauthorized access to sensitive Configurator data. Both affect EBS versions 12.2.3–12.2.14, with public exploits now circulating online.
In response to the severity and active exploitation of these vulnerabilities, Ridge Security is releasing an emergency plugin update. This accelerated deployment enables organizations to immediately validate their Oracle EBS exposure with exploitation-based detection, delivering the certainty needed to prioritize emergency patching efforts. When ransomware groups are actively weaponizing vulnerabilities, waiting for the next scheduled release isn’t an option.
From Zero-Day to Mass Exploitation
In June 2025, an Oracle EBS zero-day exploit appeared for sale on dark web markets for approximately $70,000. By August 9th, Clop (GRACEFUL SPIDER) weaponized it in mass extortion campaigns targeting organizations across finance, manufacturing, healthcare, and government sectors. Victims received ransom demands by late September claiming data exfiltration from their EBS environments.
On October 3rd, a group called “Scattered Lapsus$ Hunters” leaked the proof-of-concept exploit on Telegram. Oracle responded within 24 hours with emergency patches for CVE-2025-61882. By this point, dozens of organizations had already been compromised.
How RidgeBot Validates Both Vulnerabilities
Traditional vulnerability scanners rely on version checks or passive fingerprinting, generating false positives that waste security teams’ time. RidgeBot takes a fundamentally different approach: it validates vulnerabilities exactly as real attackers would do, providing definitive proof of exploitability with zero false positives.
RidgeBot replicates the actual attack chain used by threat actors:
- Authentication Bypass: RidgeBot sends specially crafted requests to /OA_HTML/SyncServlet to verify the authentication bypass vulnerability
- XSLT Template Injection: It uploads a controlled XSLT payload through /OA_HTML/RF.jsp and /OA_HTML/OA.jsp endpoints, mirroring the attacker’s technique
- Out-of-Band Confirmation: The payload contains a callback URL to RidgeBot’s controlled infrastructure. When code execution succeeds, the target server makes an outbound connection to RidgeBot’s callback server
- Validation: RidgeBot confirms the callback originated from the target system, providing cryptographic proof that remote code execution was achieved
This isn’t theoretical detection, its real-world exploitation performed in a controlled manner, giving you absolute certainty about your exposure.
This approach eliminates false positives by requiring real-world proof that the server processed attacker-controlled input and made external connections, exactly what an attacker would achieve during reconnaissance.
Conclusion
The dual disclosure of CVE-2025-61882 and CVE-2025-61884 completes the devastating zero-day lifecycle: from underground sale to ransomware weaponization to public disclosure, all within four months. With Clop actively exploiting both vulnerabilities, public exploits democratizing access, and CISA’s KEV catalog confirming mass targeting, unpatched Oracle EBS environments face certain compromise.
Traditional vulnerability assessment methods that rely on version checking or passive detection are insufficient for this threat. Runtime is the new battleground, and proactive visibility through active exploitation validation is the only defense.
The time to act is now. RidgeBot provides the certainty you need to prioritize remediation efforts and validate that your defenses actually work against real-world attack techniques.
RidgeBot Detection and Exploitation
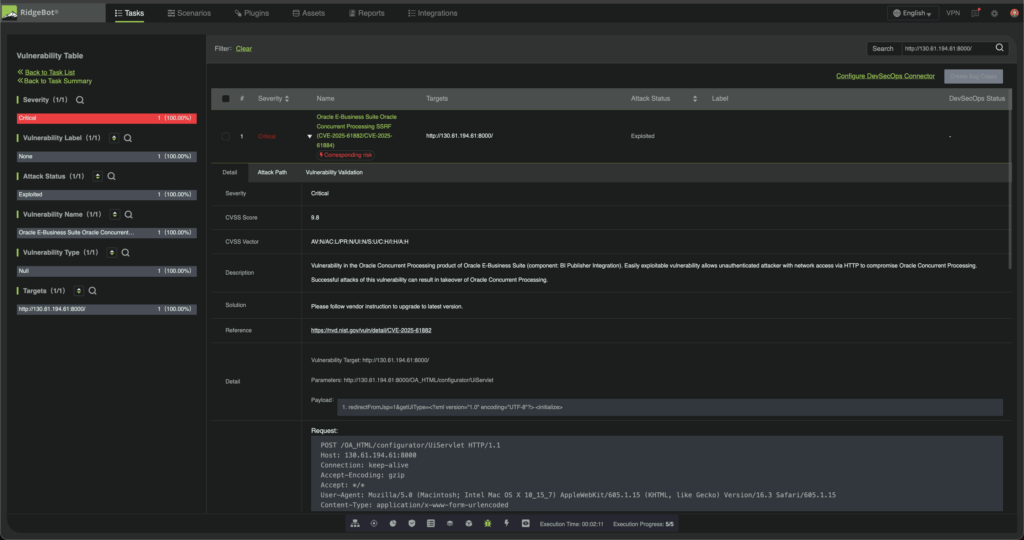
Figure 1: Screenshot of RidgeBot’s detection of Oracle EBS CVEs
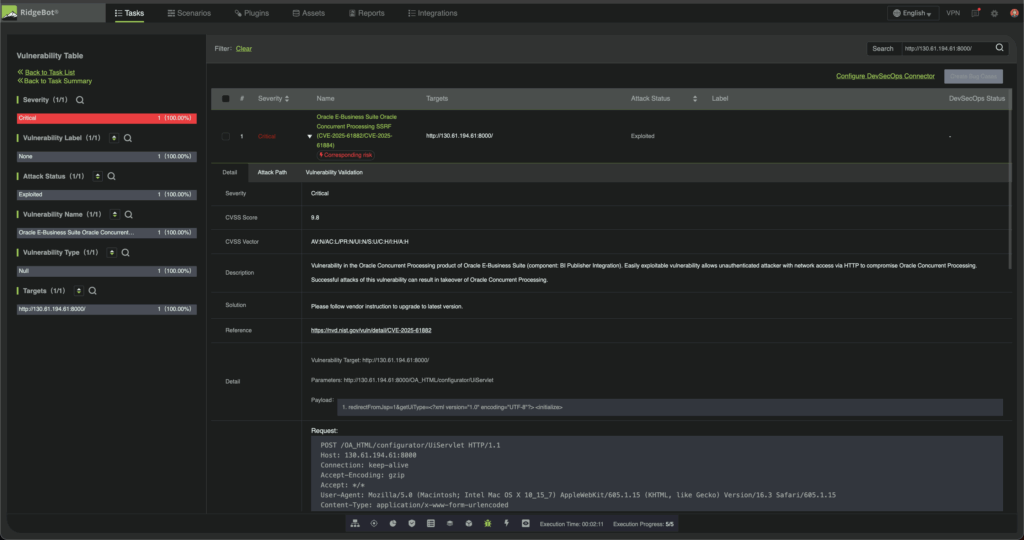
Figure 2. Screenshot of RidgeBot’s validation of Oracle EBS CVEs
