In July 2025, multiple critical vulnerabilities collectively known as “ToolShell” and tracked as CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771, were discovered in Microsoft SharePoint Enterprise Server. These flaws, actively exploited in the wild, allow unauthenticated remote code execution on vulnerable on-premises servers. SharePoint’s integration with other Microsoft services makes compromised systems a high-value target for deeper network intrusions.
CVE-2025-53770 stands out as one of the most severe SharePoint vulnerabilities to date, and organizations running on-premises SharePoint should treat it as a likely compromise. This is not a simple “patch and move on” scenario, if attackers gained access before the update, they may still be active in the environment, leveraging stolen keys or hidden backdoors to maintain persistence. Proactive remediation and ongoing monitoring are essential to ensure the threat is fully eradicated.
Exploitation typically targets the /layouts/15/ToolPane.aspx endpoint with a crafted HTTP request and spoofed Referer header to bypass authentication. Attackers then upload a malicious .aspx file to extract cryptographic keys from the server, enabling the creation of signed __VIEWSTATE payloads for advanced deserialization-based RCE. This attack chain has been observed in sectors like finance, energy, education, and healthcare, with ransomware often deployed as the final stage.
The emergence of ToolShell highlights the urgent need for continuous and proactive vulnerability management. In response, Ridge Security has swiftly developed RidgeBot® plugins capable of detecting and safely exploiting vulnerabilities such as CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771 within controlled testing environments.

Fig1: RidgeBot discovers SharePoint ToolShell vulnerability

Fig2: RidgeBot SharePoint attack logs
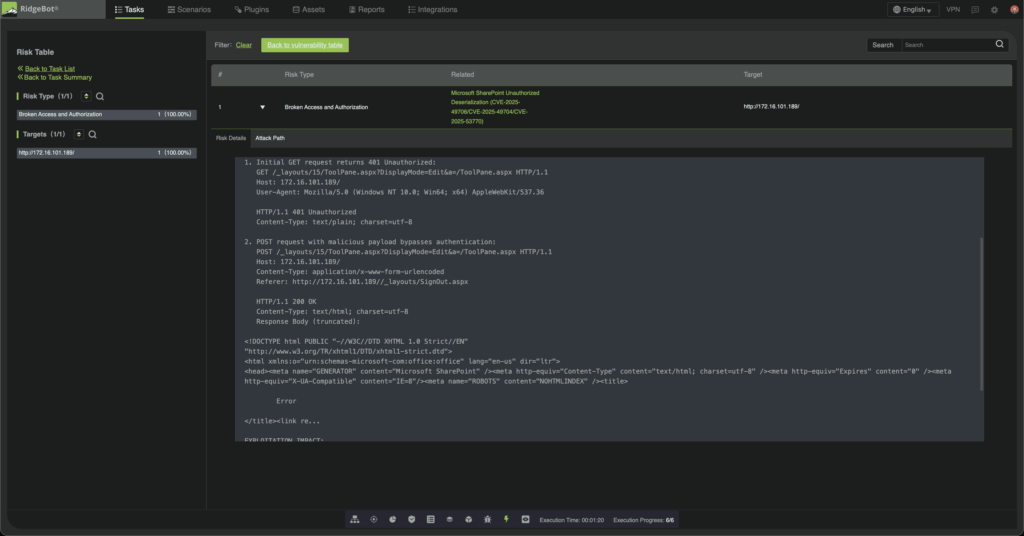
Fig3: RidgeBot Confirms SharePoint Auth Bypass (CVE-2025-49706/CVE-2025-53771)
RidgeBot’s automated penetration testing platform simulates real-world attacker behavior against SharePoint environments, identifying vulnerabilities, validating exploitability, and delivering actionable remediation guidance. These plugins provide detailed evidence—such as attack logs and proof-of-exploit screenshots—enabling organizations to remediate issues before malicious actors can weaponize them.
Even trusted platforms like SharePoint can harbor critical flaws with significant consequences. By reducing the attacker’s window from months to hours, RidgeBot empowers security teams to stay ahead of evolving threats. Backed by threat intelligence, vulnerability research, and AI-driven decision-making, RidgeBot replicates skilled adversary tactics to uncover weaknesses, from initial vector discovery to exploitation, and delivers continuous, automated protection for modern enterprise environments.
