Hafnium is a cyber espionage group with alleged ties to the Chinese government. They are responsible for a global wave of cyberattacks and data breaches which began in January 2021 after several zero-day exploits were discovered in Microsoft Exchange Servers. It gives attackers full access to user emails and passwords, administrator privileges on the server, and access to connected devices on the same network. Approximately, 60,000 organizations have been compromised by these vulnerabilities, and tens of thousands are still unaware that they are exposed to these Microsoft Server flaws.
Since Microsoft released the Exchange Server patches on March 2, 2021 cyberattacks targeting these vulnerabilities have dramatically increased. Criminals know that the window of opportunity is closing and they are trying to compromise as many servers as possible before they are patched.
Attackers typically install a backdoor that allows full access to impacted servers even if the server is later patched and is no longer vulnerable to the original exploits. Therefore, it is critical to update unprotected servers before they are discovered by cybercriminals. A temporary fix would be to place the Exchange server inside a VPN to separate port 443 from external connection requests.
Which Servers are Impacted by the Zero Day Exploits?
The following servers need to be updated immediately:
- Microsoft Exchange Server 2013 – 15.00.1497.012
- Microsoft Exchange Server 2016 – 15.01.2106.013
- Microsoft Exchange Server 2019 – 15.02.0721.013
- Microsoft Exchange Server 2019 – 15.02.0792.010
Only Exchange software is affected by these vulnerabilities and not Exchange Online.
Methodology
There are four Common Vulnerability Exposures (CVEs) being exploited:
- CVE-2021-26855
- CVSS 9.1 (critical)
The attack chain begins with the exploration of this flaw, also known as a Server-Side-Request-Forgery (SSRF) vulnerability. All that is required for an attacker to exploit the flaw is to know the IP address or fully qualified domain name (FQDN) of an Exchange Server and the email account they wish to target. The vulnerable exchange server would also need to accept untrusted connections over port 443. Successful exploitation of this flaw would allow the attacker to authenticate to the Exchange Server.
- CVE-2021-34523
- CVSS 7.5 (high)
This is another Microsoft Exchange Remote Code Execution vulnerability where validation of access token before PowerShell is improper. An adversary using this flaw can gain “System” user access which in turn has “Admin” access.
- CVE-2021-26858 and CVE-2021-27065
- CVSS 7.8 (high)
Both CVE-2021-26858 and CVE-2021-27065 offer similar system compromise capabilities to CVE-2021-34523 when they are exploited.
Only after privileged access is authenticated via CVE-2021-26855 can these flaws be exploited. Upon successful compromise an attacker will be permitted to inject malicious code into any path on the Exchange server. Hafnium uses these flaws to deploy web shells – otherwise known as backdoors, to get remote access to the server. This makes injecting malicious commands and the deployment of ransomware possible even after these CVEs have been patched.
How to Determine if Your Organization is Impacted
Ridge Security provides a comprehensive analysis of your threat environment. It not only scans for vulnerabilities but it provides step-by-step kill chains to depict how the vulnerability can be exploited. It also provides guidance on remediation.
To determine if you are at risk you need to open the vulnerability table and look for CVE-2021-26855 since all remaining flaws can only be exploited after this one has been compromised. If CVE-2021-26855 is detected, you can infer that all other vulnerabilities have been exploited.
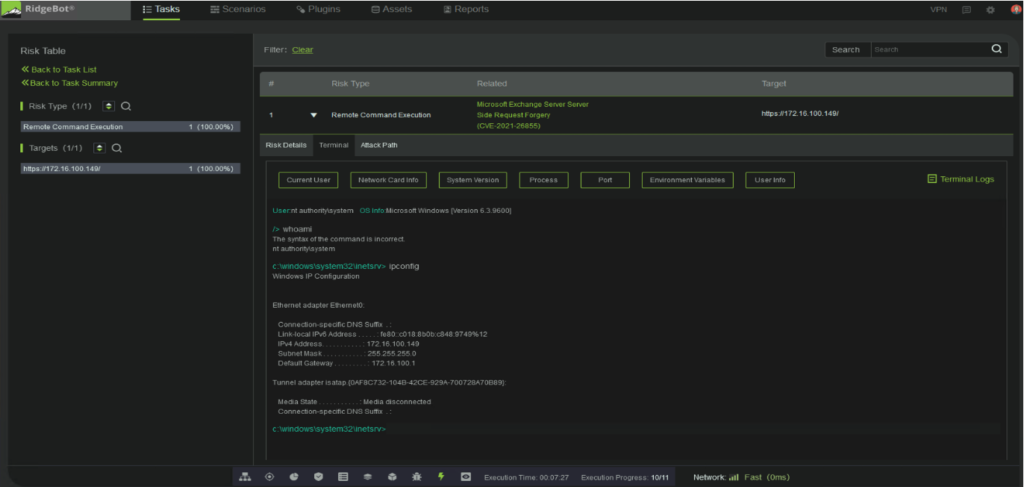
Figure 1: RidgeBot discovered ProxyLogon as Risk (vulnerability successfully exploited)
You will note that the vulnerability table contains a notation when there are other corresponding risks or vulnerabilities. These vulnerabilities will be listed under the corresponding severity of high, medium, or low. In addition, the Risk Table shows risk details and provides a real-time terminal interface into the remote command interfaces.
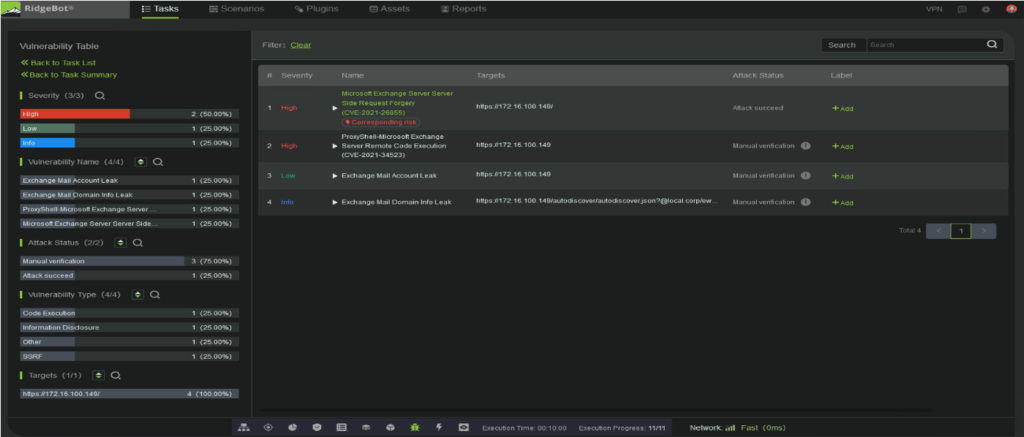
Figure 2: Evidence that shows the shell has been compromised
Unprotected servers need to urgently be updated before they are discovered by cybercriminals. If you discover that you’re exposed to CVE-2021-26855 update the servers that are externally facing first.
The Microsoft Security Response Center (MSRC) posted an out-of-band Common Vulnerabilities and Exposures (CVE) release on March 2, 2021, urging its clients to patch their Exchange servers. On March 15th, Microsoft released a one-click PowerShell tool, The Exchange On-Premises Mitigation Tool, which installs the specific updates protecting against the threat. It also runs a malware scan which detects installed web shells and removes detected threats. This is recommended as a temporary mitigation measure, as it does not install other available patches and updates.
How Do I Know if I Have Been Compromised?
You can check if your organization has already been exploited by running the Microsoft Indicators of Compromise (IOC) detection tool.
Microsoft is continuously updating its feed of detected Malware hashes and malicious file paths associated the latest Exchange Server exploits.
What to Do if You’ve Been Compromised
The United States Government Cybersecurity and Infrastructure Security Agency has created a victim response guide specifically for CVE-2021-26855. The guide, known as CISA Alert AA21-062A, explains how to conduct a forensic analysis to assist remediation efforts.
