Citrix NetScaler is a networking product that optimizes, secures, and controls the delivery of enterprise applications. It functions primarily as a high-performance load balancer, SSL offloader, application firewall, and content switch, supporting both on-premises and cloud deployments. Designed for scalability and security, NetScaler is often used in environments requiring seamless application performance, such as Virtual Desktop Infrastructure, e-commerce, and SaaS platforms. It holds a strong niche presence, particularly in industries like healthcare, finance, and government. It is a major player in traditional data center and hybrid environments.
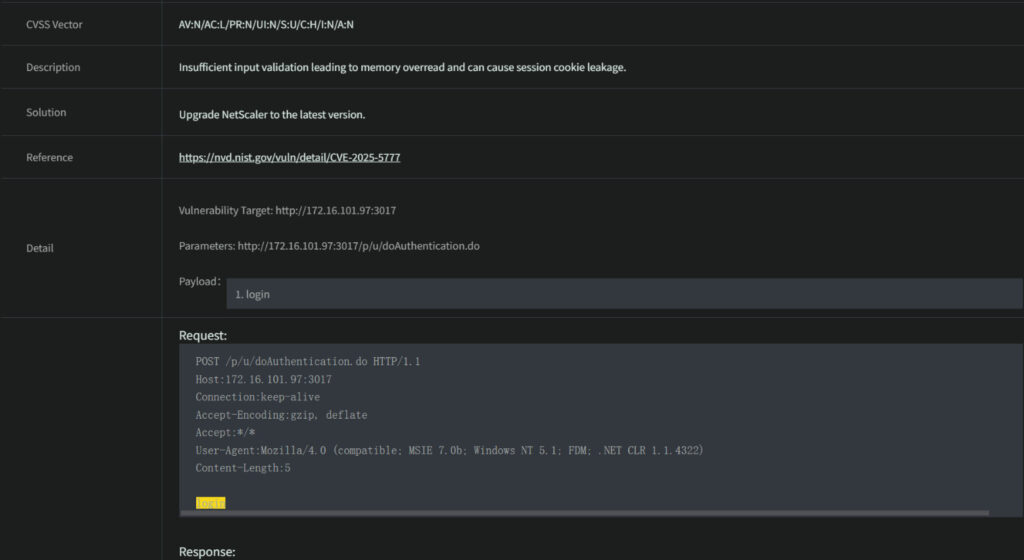
On 2025/6/17, NIST published CVE-2025-5777, a memory overread vulnerability which allows remote unauthorized attacker to read sensitive contents from the server’s memory. The affected NetScaler ADC and NetScaler Gateway versions are 14.1 BEFORE 14.1-43.56, 13.1 BEFORE 13.1-58.32, 13.1-FIPS and NDcPP BEFORE 13.1-37.235-FIPS and NDcPP, 12.1-FIPS BEFORE 12.1-55.328-FIPS, and NetScaler ADC and NetScaler Gateway versions 12.1 and 13.0. Because of the ease to exploit this vulnerability and the great influence, NIST assigned CVSS score 7.5. Moreover, it is recently added to CISA Known Exploited Vulnerabilities Catalog on 2025/7/10, which means that there have already been known exploits in the wild.
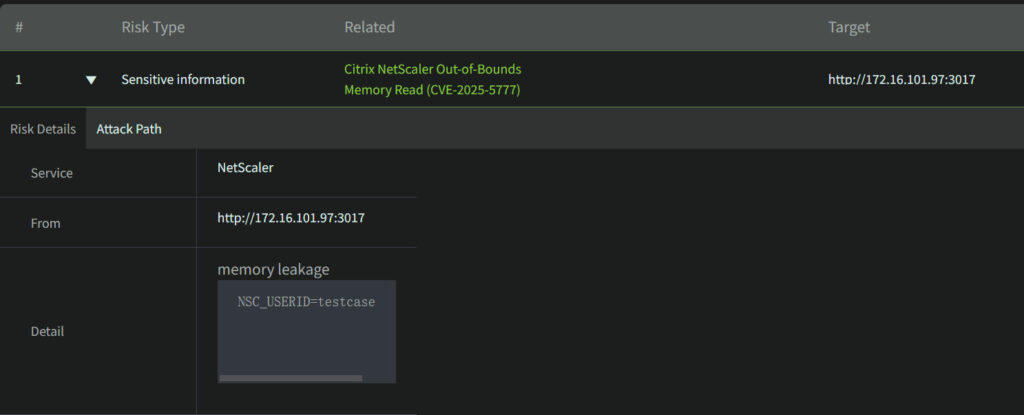
Attacker cannot read certain part of memory by this vulnerability, but through multiple trials, besides sensitive information in memory, they will be able to get session tokens which allow them to directly log in for further attacks. This can lead to the control over the whole affected system.
The dedicated engineer team of Ridge Security takes immediate action in response to the update of CISA KEV Catalog. At the time of writing this blog, we are proud to announce that the plugin to scan this CVE is going to be included in the new release. Once this CVE is found, it is strongly recommended to install the relevant updated versions as soon as possible.