Jack has now recovered from his ransomware incident. The Windows® Servers have been recovered and upgraded to the latest security patches. Jack has also restricted the remote access and disabled any unused network services and network ports.
But with this run with ransomware still fresh on his mind, Jack could not help but wonder about hidden malware in his servers. Jack was rightfully worried: the recent Ransomware headlines – Colonial Pipeline, JBS, and Kaseya further reinforced his concerns and caused even more anxiety. Ransomware continues to dominate the news with on-going warnings of notorious ransomware gangs behind hacks from Managed Service Providers to small, and medium-sized businesses globally.
Fortunately for Jack, he has friends in the network security space. After consulting the subject matter expert, Jack was advised to solicit a Penetration Testing service to do a sweep of his servers to find potential vulnerabilities. While Jack knew it was a good idea, he had neither the time nor resources to initiate this project himself. Doing a Google search landed Jack on Ridge Security’s website.
Jack decided to give RidgeBot® from Ridge Security a try. He only needs to install RidgeBot® on a virtual machine in his office. Within an hour, he was able to start the Pen Testing task with only the Windows® Server IP address.
Jack is pleasantly surprised. RidgeBot® automatically performs Pen Testing and provides test results within a few hours, depending on the environment. Using RidgeBot®, Jack has found additional vulnerabilities that were successfully exploited by RidgeBot on his Windows® Server.
Instinctively, he decides to leverage RidgeBot® in the office to test another mission-critical Windows® server on a remote site.
Here are the results by RidgeBot®:
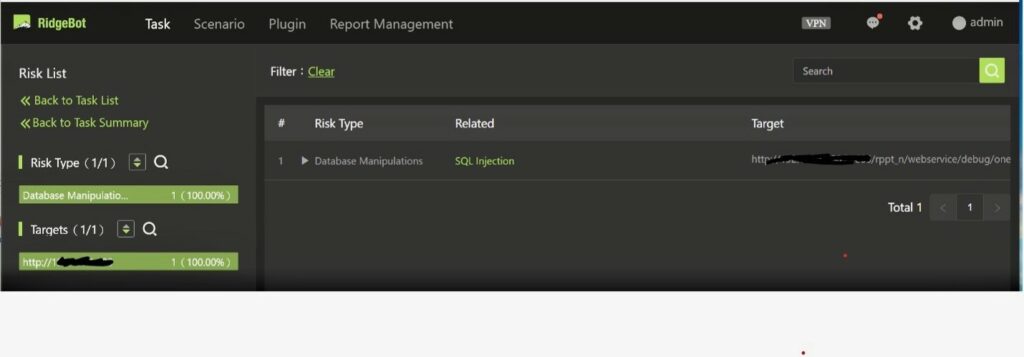
RidgeBot® found one Risk in his Windows® Server.
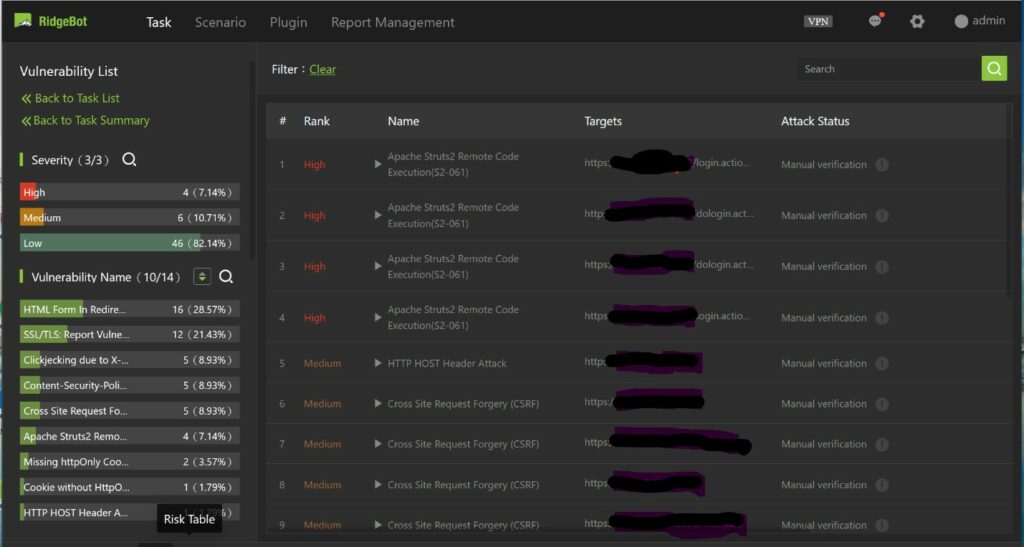
On his remote target, RidgeBot® has identified several Apache Strut-2 RCE Vulnerabilities.
This vulnerability would not bode well for Jack. Hackers can easily use SQL injection techniques to get elevated privileges to compromise the Windows® Server in his office. Hackers can then launch additional attacks from this server to get control of other connected servers running off-premises.
Using RidgeBot®, Jack found two Windows® Servers with exploitable vulnerabilities within hours, and he has effectively avoided another potential Ransomware attack.
When it comes to cybersecurity — no one is safe. And it is no longer just about network access or having a security policy. It is the ability to think like a hacker and use automated Pen Testing tools like RidgeBot®, to continuously be on the lookout for exploitable vulnerabilities in servers, websites, applications, etc.
Jack’s lesson: It is important to be vigilant and have a healthy paranoia to stay one step ahead in this never-ending cybersecurity game.