This is a true story.
April 26, 2021: just a regular Monday morning during the year of a global pandemic, when most tech companies still allowed their employees to work from home. Traffic was light on the road and the parking lot was nearly empty when Jack pulled his red Cherokee in front of his office building. Jack came to the office occasionally to check up on things. This morning, he had driven up to the office to maintain their Windows® servers.
Jack is the head of this office, the sales and research branch of a global company. With only a handful of employees working in this branch office, Jack – like many people running a small business – wears many hats. He is the Research VP, Software Engineer, as well as the IT Support, all in one.
For his research work, Jack needs to constantly log into his servers to access data and applications. Since the lock down, to make work-from-home possible, Jack has had to open many service ports to gain access. For a long while, the entire last 12 months, everything worked just fine… until Monday, April 26.
On this day, when he tried to log in as usual, the password did not work. He tried multiple times in vain, and eventually had to use the PE disk to remove the admin password for the server. He got in but was immediately shocked to find that many files were encrypted, and the file types were changed to Eking.
He then saw this fateful note:
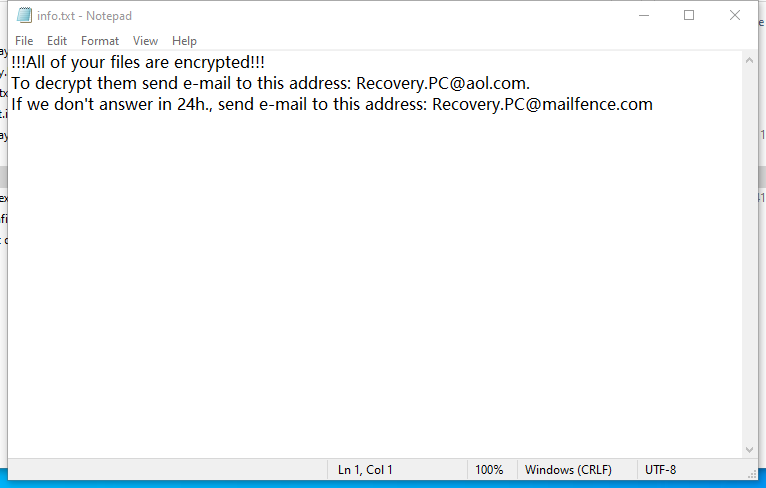
By googling Eking, Jack realized that his servers were infected by a type of ransomware called Phobos.
Jack thought about it for a second and shook his head: “How ironic! When people zealously protect themselves from COVID-19, their servers get the ‘lucky draw’ in their world.” As an experienced tech geek, Jack naturally understood the security risks of publicly open service ports. But who would target a small business? After all, they are one of millions of companies in Silicon Valley, and a small one that operated under the radar.
But Jack had no time to wonder “why,” but soon buried himself into how to recover.
This is what Jack learned about Phobos:
- Phobos is named after the Greek god Phobos, son of Ares and Aphrodite and twin brother of Deimos. Phobos was the god and personification of fear and panic. (This anecdote is for people who love both Greek mythology and cyber security).
- Phobos ransomware appeared at the beginning of 2019 and people believe that it is tied to the Dharma family. Phobos is a ransomware that is distributed via hacked Remote Desktop (RDP) connections. Bingo! Jack’s servers have quite a few RDP services and he kept it open throughout the work-from-home mandate for access.
As it turned out, among their four Windows® servers, two Windows® 2019, two Windows® 2016, the two Windows 2016 which hosted their Ordering System (all orders and every transaction) were compromised. The Windows 2019 servers remained intact.
Was Jack able to recover all their orders? Did he pay the $3000 ransom? To be continued next week …