CISA has added CVE-2025-55182 to its Known Exploited Vulnerabilities (KEV) Catalog, an urgent warning for any organization running React Server Components or Next.js. This critical flaw, found in the RSC Flight protocol, enables unauthenticated remote code execution and has already been patched by Meta and Vercel. Unfortunately, exploitation is well underway.
CVE-2025-55182 (CVSS 10.0) is being actively weaponized, with publicly available proof-of-concept exploit code and widespread targeting by multiple threat groups. The affected ecosystem, React 19.x and Next.js 14-16, represents some of the most heavily deployed frameworks on the modern web.
As the threat landscape shifts rapidly, Ridge Security is releasing an emergency plugin update that enables organizations to immediately assess their exposure using exploitation-based validation. When attackers are moving fast, waiting for scheduled release cycles is no longer an option.
From Disclosure to Mass Exploitation in 24 Hours
The speed of this attack chain has been unprecedented.
- December 3, 2025: Researcher Lachlan Davidson publicly discloses CVE-2025-55182.
- Within 12 hours, working proof-of-concept exploits appear online.
The scale of exposure is enormous:
- Censys: ~2.15 million internet-facing services potentially vulnerable
- Shadowserver: 28,964 confirmed vulnerable hosts (as of December 7)
React and Next.js are everywhere—this is not a niche edge case. The internet’s front end has suddenly become a massive attack surface.
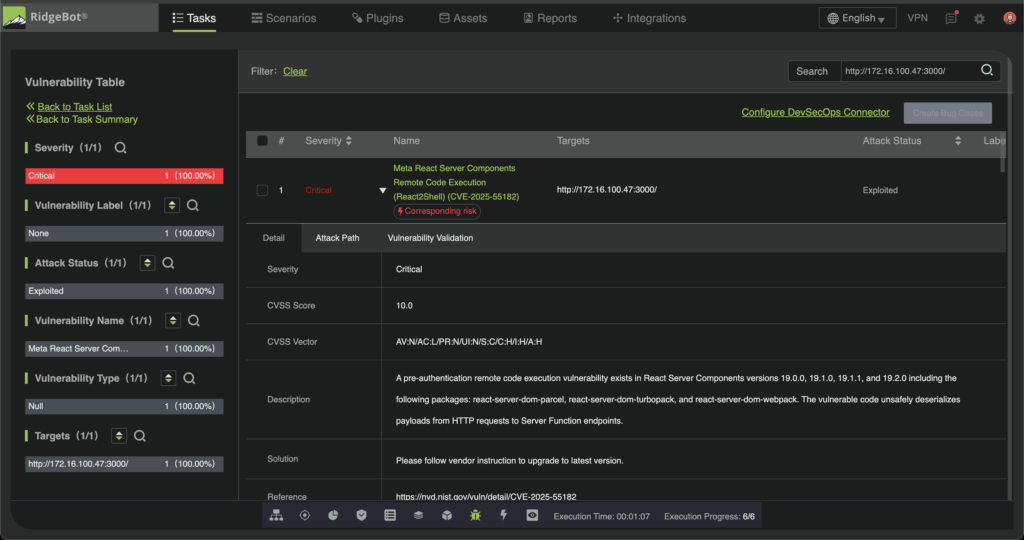
How RidgeBot Validates React2Shell With Zero False Positives
Most vulnerability scanners rely on version checks or passive indicators, often creating noise and false positives. RidgeBot takes a different approach: it validates vulnerabilities by safely reproducing attacker behavior. The result is definitive, cryptographic proof of exploitability.
RidgeBot’s exploitation-based detection process includes:
1. RSC Endpoint Discovery: RidgeBot enumerates exposed React Server Component and Server Action endpoints.
2. Flight Protocol Exploitation: Specially crafted RSC Flight payloads trigger the insecure deserialization flaw at the heart of CVE-2025-55182.
3. Out-of-Band Callback Verification: Payloads include a callback URL to RidgeBot-controlled infrastructure. If execution succeeds, the targeted server makes an outbound connection.
4. Business risk demonstration: With vulnerability confirmed. RidgeBot uses further exploit payloads and proceeds to dump files such as /etc/passwd in Linux and win.ini for Windows systems to demonstrate real business risks.
This method mirrors real attacker actions, but under controlled conditions that eliminate false positives entirely. If RidgeBot confirms the callback, exploitation is real. If it doesn’t, the system is not exploitable. Security teams get clarity, not guesswork.
Take-aways
React2Shell highlights just how quickly modern vulnerabilities can escalate from disclosure to global exploitation. In less than 24 hours, CVE-2025-55182 evolved from a research finding to a nation-state weapon, with widespread scanning and active intrusions following immediately afterward. CISA’s KEV inclusion underscores the severity and the ongoing mass targeting.
In this environment, traditional version-based detection simply cannot keep up. Runtime validation, proving actual exploitability through controlled, real-world techniques, is now critical for accurate risk assessment.
RidgeBot delivers that capability. By confirming exploitation through active validation, it gives security teams the certainty they need to prioritize patching and protect exposed environments before attackers reach them.
The threat is active. The attack surface is massive. The window for response is narrow.