OpenSSH is the premier connectivity tool for remote login with the SSH protocol. It provides a large suite of secure tunneling capabilities, several authentication methods, and sophisticated configuration options. It is the default SSH implementation in most UNIX and Linux distributions and is also available for other platforms, such as Windows. Therefore, it is extremely popular and widely used across various domains, including system administration, network management, and secure communications.
On July 1, 2024, NIST published CVE-2024-6387, a vulnerability susceptible to a signal handler race condition that allows attackers to perform remote code execution with root privileges on glibc-based Linux systems. This vulnerability is a re-introduced version of an old vulnerability, CVE-2006-5051. Recent code changes accidentally removed the previous fix, causing this vulnerability to resurface. Due to the widespread usage of the OpenSSH Server, NIST assigned it a CVSS score of 8.1. While exploitation scripts are available on the internet, there have been no reports of exploitation in the wild yet. Any unpatched version between 8.5p1 and 9.8p1 is at risk.
The dedicated engineering team at Ridge Security took immediate action in response to this new vulnerability. At the time of writing this blog, we are proud to announce that a plugin to detect this CVE has already been included in the new release. With RidgeBot and its latest plugin library, version 4.57, customers can easily and quickly inspect whether their entire IT infrastructure has been impacted by this vulnerability.
During our research, we found that while the exploit of this vulnerability is very disruptive, it is very hard to trigger. As this vulnerability involves a signal handler race, the exploitation takes a long time and generates a lot of traffic. On average, it takes roughly 10,000 attempts to successfully trigger the race condition. With 100 connections (MaxStartups) allowed every 120 seconds (LoginGraceTime), it typically takes about 3-4 hours to succeed. Considering the need to bypass ASLR (Address Space Layout Randomization), a full exploit to achieve remote root access might take around 6-8 hours. We urge customers to fix it as soon as they can before an exploit can be successfully executed.
With Ridge Securit’s RidgeBot AI-powered automated testing, customers can quickly find all potential risks in their entire network. Once vulnerabilities are discovered, RidgeBot provides detailed reports including the type, severity, description, and other pertinent details. With this information, it will be easy to understand what the vulnerabilities are, their impact, and how to patch them. Given its disruptive nature, RidgeBot chose not to develop an exploit plugin for this vulnerability.
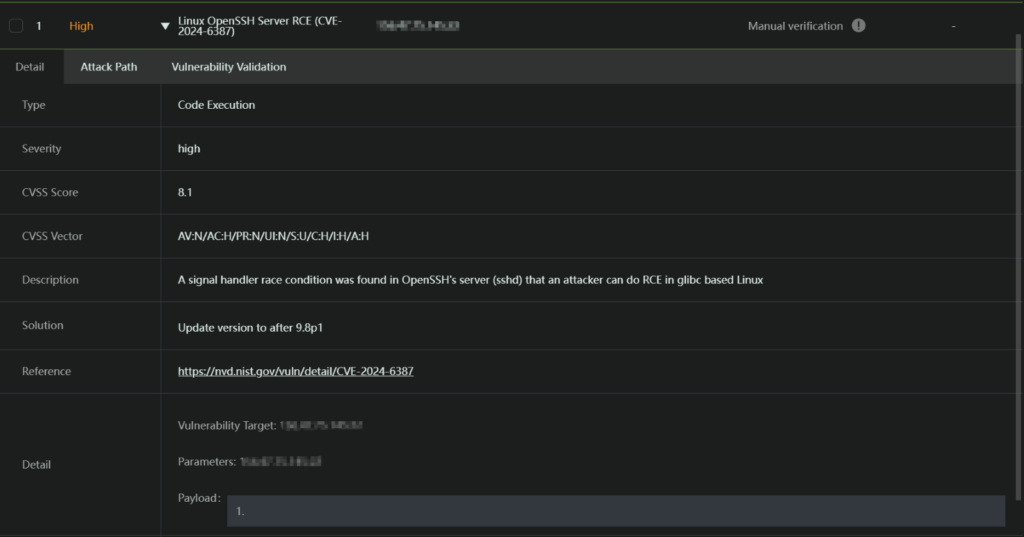
Figure 1: Vulnerability report for CVE-2024-6387
In the Information Age, cyber threats are everywhere. Ridge Security continuously monitors emerging vulnerabilities to protect our customers. With our ever-growing threat intelligence database, RidgeBot provides unparalleled defense against evolving cyber threats, giving you peace of mind and robust protection in an ever-evolving threat landscape. Please contact us to request a free trial.