Ransomware is a money-making proposition for bad actors seeking to monetize hijacked data from an organization’s compromised apps and systems. Let’s cut to the chase, and call it out for what it really is – extortion.
Bad actors use many different tactics, techniques, and procedures in their ransomware exploits. They have perfected a variety of behaviors, processes, and strategies to improve the results of their attacks. As victimized organizations have become less inclined to pay ransoms, bad actors have developed new approaches to extract money. Beyond holding data ransom by encryption, they’re combining encryption with other methods to encourage the probability of payments.
In these combination attacks, first the bad actors gain access to the organization’s assets and exfiltrate their data, then they encrypt it. If the organization refuses to pay for the decryption key, the hacker may publicly expose the exfiltrated data to disgrace and harass the organization to its customers, investors and the public at large. The intent is to threaten the organization with the possibility of damaging their brand, business, and financial reputation. They may also auction off the stolen data on the dark web to at least make some money for their efforts.
RidgeBot outmaneuvers ransomware schemes
RidgeBot auto-discovers your assets, scans them, and then proceeds to ethically exploit the vulnerabilities found just as a hacker would. Each test includes a report that alerts you to the potential ramifications if the vulnerability was to be successfully exploited by a bad actor. The report also shows you the exact attack path that allowed the asset to be compromised. With this detailed and accurate information, you can quickly and proactively eliminate all the vulnerabilities within your network and digital assets.
RidgeBot includes ransomware protection with a template specifically designed for combating ransomware attacks. There are many template capabilities available, such as scanning for 270 high-profile ransomware entry point vulnerabilities, launching attacks to exploit these vulnerabilities, and detailed reporting on exactly how the successful testing exploitations were achieved.
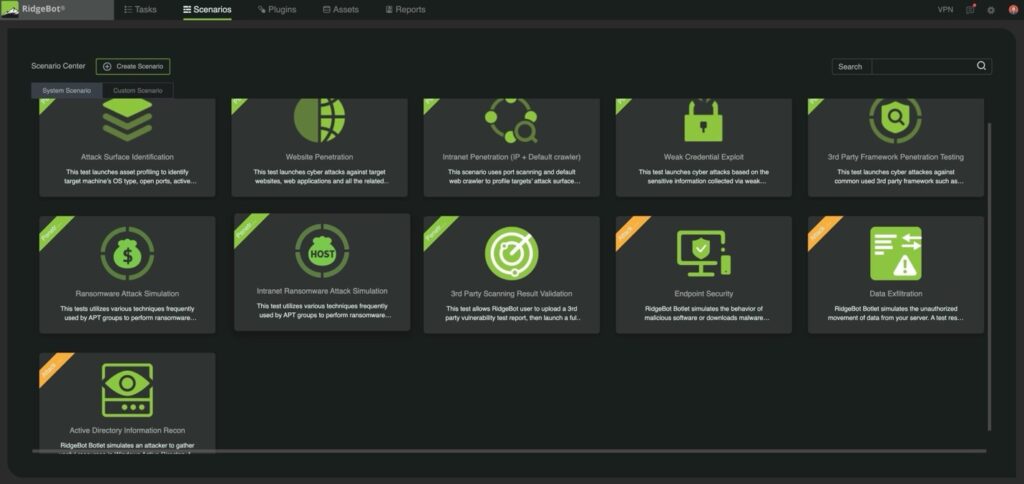
Figure 1: Pre-Built Ransomware Attack Testing Scenario
Running the RidgeBot ransomware template allows you to quickly and easily launch an asset scan to detect ransomware related vulnerabilities that may be present within your assets. As an integral part of the scan, RidgeBot also launches attacks to validate that the vulnerabilities found are indeed exploitable in your current environment. You can automatically run these penetration tests and attacks on demand, or on a regular schedule.
As with other vulnerability tools and tests, it is recommended you re-execute a ransomware template scan-and-exploit whenever there are any changes to your assets, such as:
- Adding a new server or device
- Upgrading software or firmware
- Installing patches
- Changing scripts or information on a web server
Any other software or hardware changes that may result in deploying a new vulnerability in your network should involve pentesting re-execution.
The RidgeBot ransomware template includes scanning and exploitation for remote code and command execution, weak passwords and credentials, server message blocks, Weblogic and other file uploads. RidgeBot scanning and exploitation also covers technical vulnerabilities such as weak credentials, file uploads, WebLogic and Struts2 Remote Code Execution vulnerabilities.
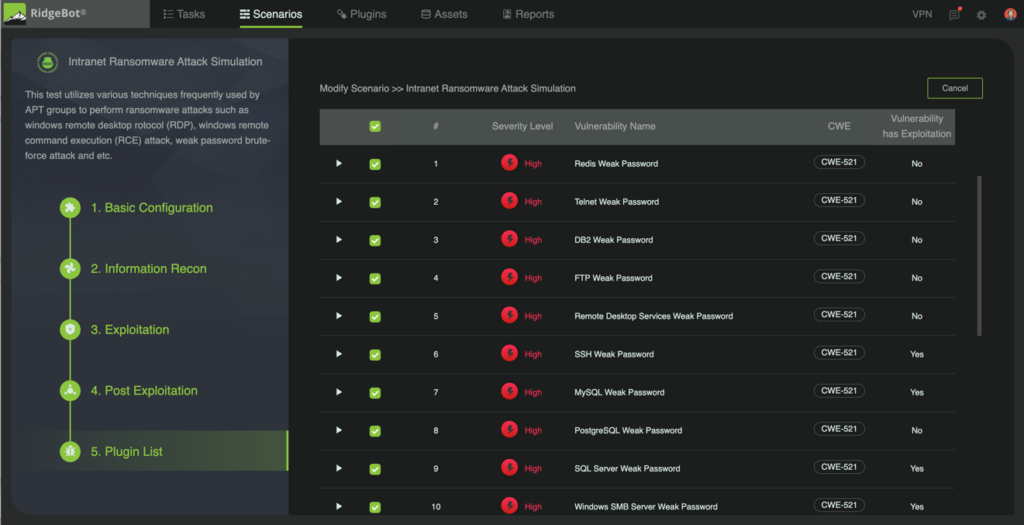
Figure 2 Weak Credential Testing over 55 Protocols and Applications
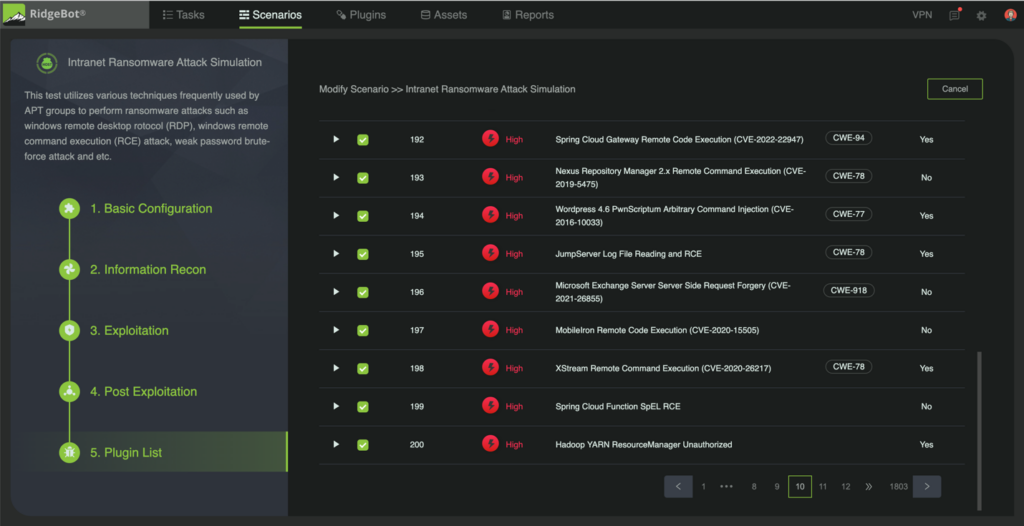
Figure 3 Example: Remote Code Execution Vulnerabilities Testing
RidgeBot scanning and exploitation capabilities can also be used to protect against the initial compromise stage of a planned attack. However, RidgeBot doesn’t protect against social engineering or phishing, nor can it help with data that has already been encrypted by a ransomware attack. Once a hacker enters your network and establishes a foothold, you will need additional tools to detect and eliminate the intrusion.
RidgeBot provides complete vulnerability and attack path visibility
RidgeBot develops a comprehensive network structure of discovered assets and shows a list of targets, exploits and vulnerabilities that were successfully penetrated during the testing process. Highlighting any one of these penetrations within the RidgeBot dashboard reveals the exact attack path that RidgeBot followed to compromise that target. This provides clear and accurate information on what types of fixes or updates are needed on specific assets within your environment to be properly secured against ransomware attacks.
Click here to learn more about how RidgeBot can protect your business.
