Should CISO’s consider adding an army of robots to their defenses?
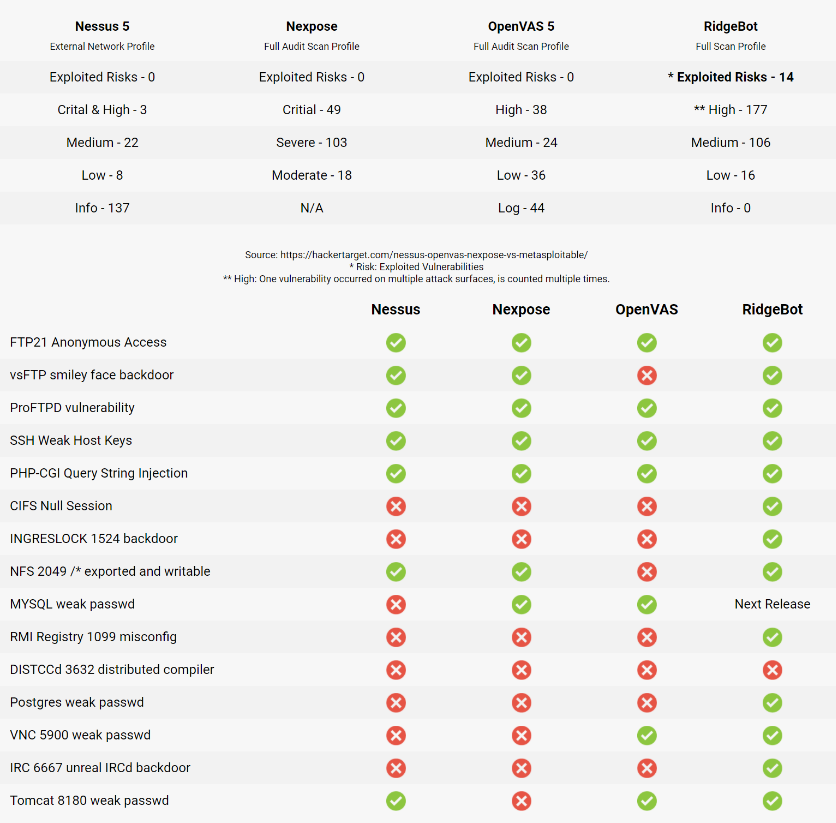
How different are they? The benchmark testing below against Metasploitable 2 (MSF2) tells you all:
- Among the top 15 designed vulnerabilities, RidgeBot™ has the most findings;
- RidgeBot™ is able to exploit 14 vulnerabilities and shows the Proof of Concept result;
- Scanners have less findings and are not able to exploit the vulnerabilities for validation.
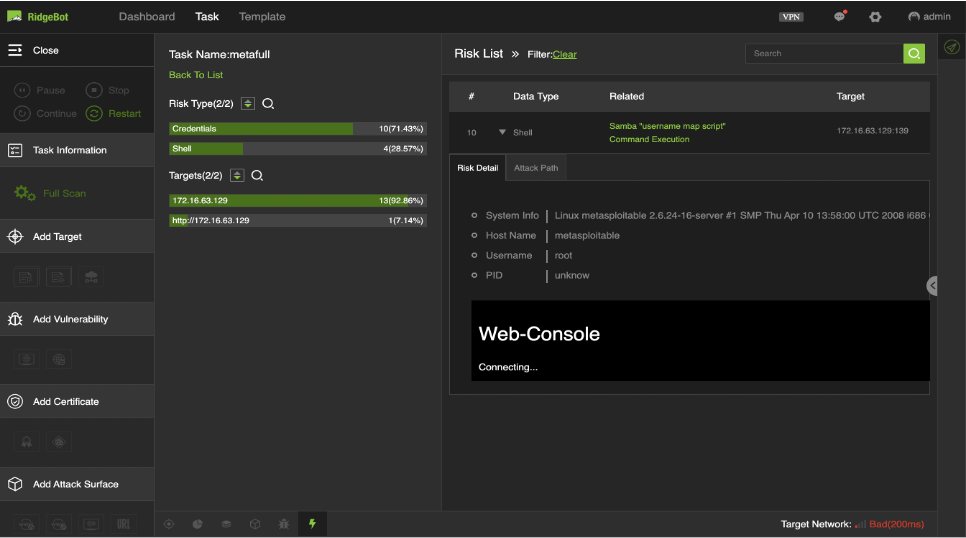
Exploit Example 1: RidgeBot™ exploited Samba “username map script” Command Execution vulnerability and successfully gain an access to the web-console
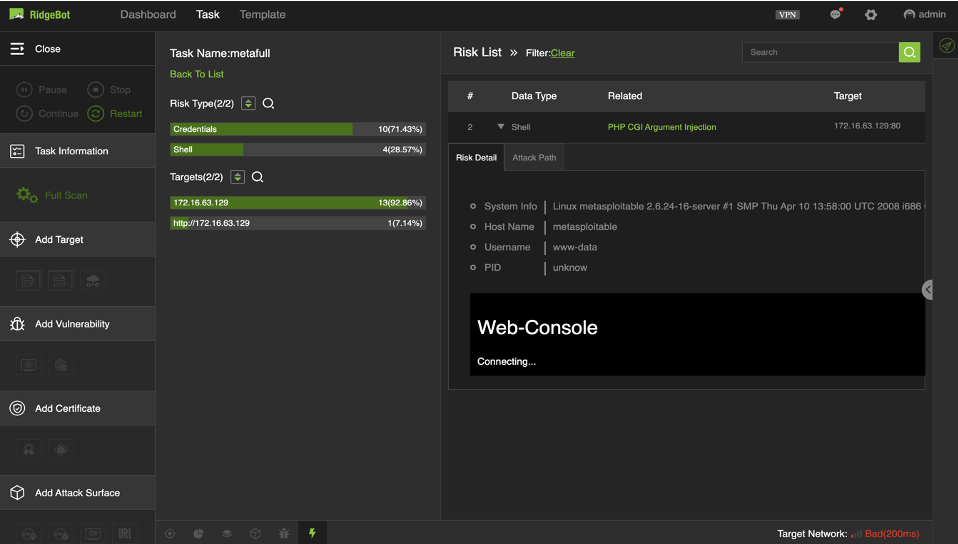
Exploit Example 2: RidgeBot™ exploited PHP CGI Argument Injection vulnerability, and get access to the web-console
Download RidgeBot™ full test report now to learn more.
