The Study of Different Approaches from 4 Well-Known Vendors
You may wonder “how does a blackbox penetration test tool know about my server information when it only has the server’s IP address?” The secret is a protocol, such as Sever Message Block (SMB), discloses that information in the response to your special requests.
In our last blog, we talked about the essential role that SMB plays in Operating System (OS) fingerprint recognition. In this blog, we will review how different vendors use SMB, and the pros and cons of each approach.
First, let’s look at Nmap’s approach. Nmap basically uses “nse script – nmap/scripts/smb-os-discovery.nse” to realize this function. Its method is shown as follows:
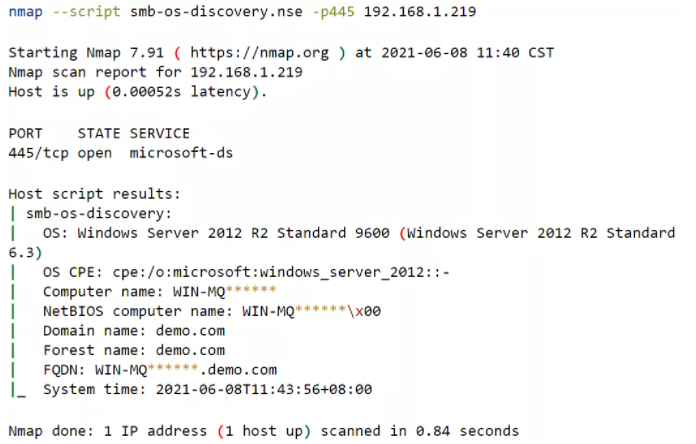
Or use the following commands to achieve the same result:

However, it has been confirmed that this approach with “smb-os-discovery.nse” cannot recognize OS of Windows Server 2016 and above. In addition, it cannot detect hosts that only support SMBv2.
Most likely Censys uses Nmap -sV option to detect SMB OS. After carefully examining Censys’s response to our test machine, we tend to get this conclusion. Due to the same flaw, it falsely detected our test machine Windows Server 2016 as Windows Server 2008 R2 -2012 microsoft -ds. (see Figure 1)
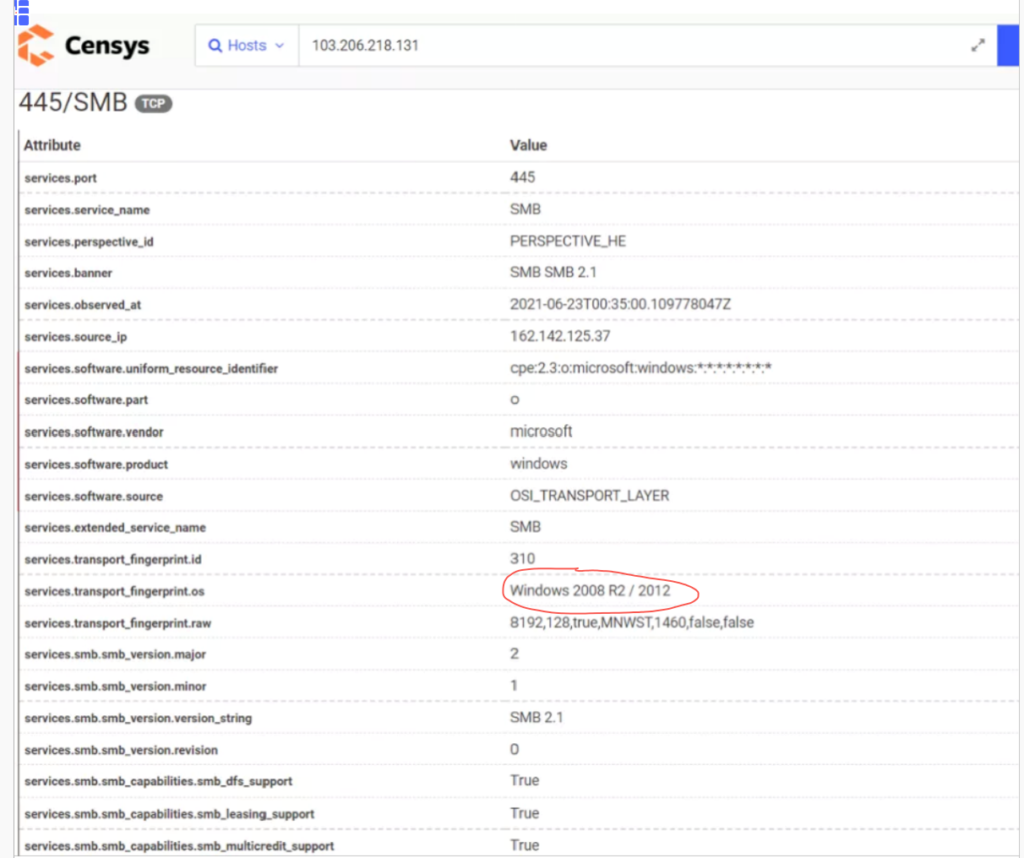
Figure 1: Censys’s OS Fingerprint Recognition via SMBv2.1
We reviewed Shodan’s OS recognition with SMBv1 (Figure 2) and SMBv2(Figure 3), and found that Shodan uses its priorietary approach to deal with OS regconition, and it scanned the common directory which is considered more intrusive scanning.
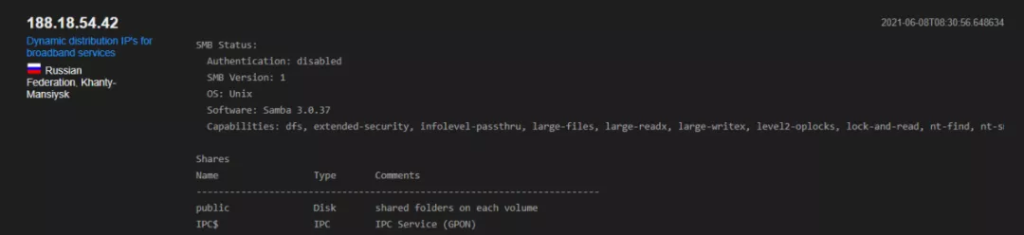
Figure 2: Shodan’s OS Recognition with SMB v1

Figure 3: Shodan’s OS Recognition with SMB v2
It’s worth mentioning that by using the following fields:
- OS: corresponding to NativeOS Microsoft defined in SMB protocol
- Software: corresponding to NaveLanMan in SMB protocol
The target’s OS can be determined by combining the information obtained from these two fields.
- Example 1: Test machine is Windows Server 2016
- Native OS field: Windows Server 2016 Datacenter 14393
- NativeLanMan field: Windows Server 2016 Datacenter 6.3
- Example 2: Test machine is Ubuntu
- Native OS field: Windows 6.1
- NativeLanMan: Samba 4.3.1-Ubuntu
In example 2, NativeLanMan shows correct information and Native OS presented a false recognition.
MSF uses “auxiliary/scanner/smb/smb_version” module to detect SMB OS. The test shows its accuracy is as good as Shodan’s. Figure 4 is MSF’s export of OS information via SMB:
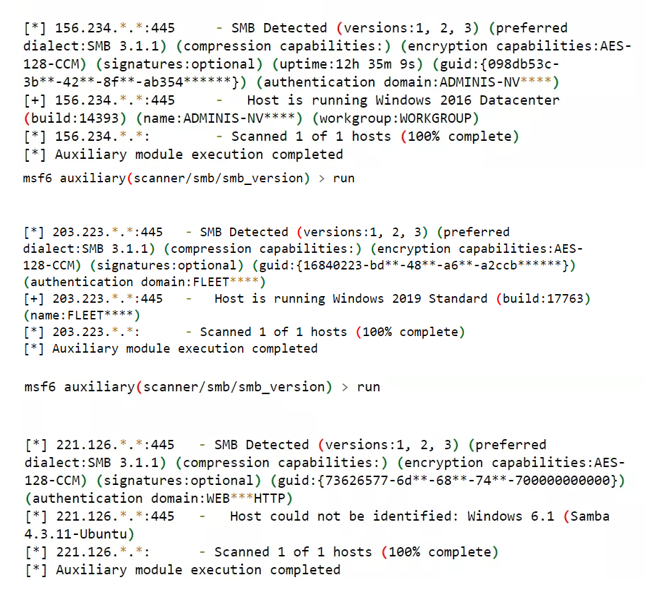
Figure 4: MSF’s export of OS information via SMB
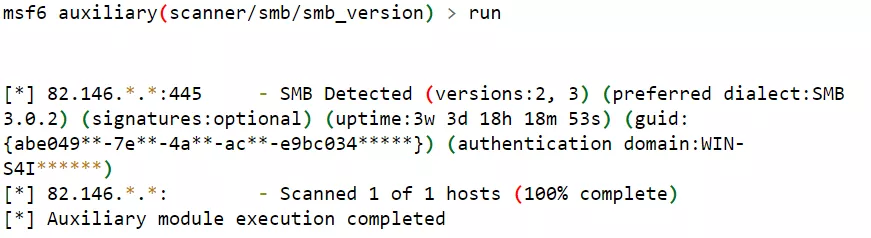
And when tested with a target that supports SMBv2 only, MSF shows relative comprehensive analysis, as shown below.
And for SMBv1 detection, MSF basically sends a request such as “Session Setup AndX Request, NTLMSSP_NEGOTIATE”. And from the packet capture showed in Figure 5, MSF also scanned the common directory.
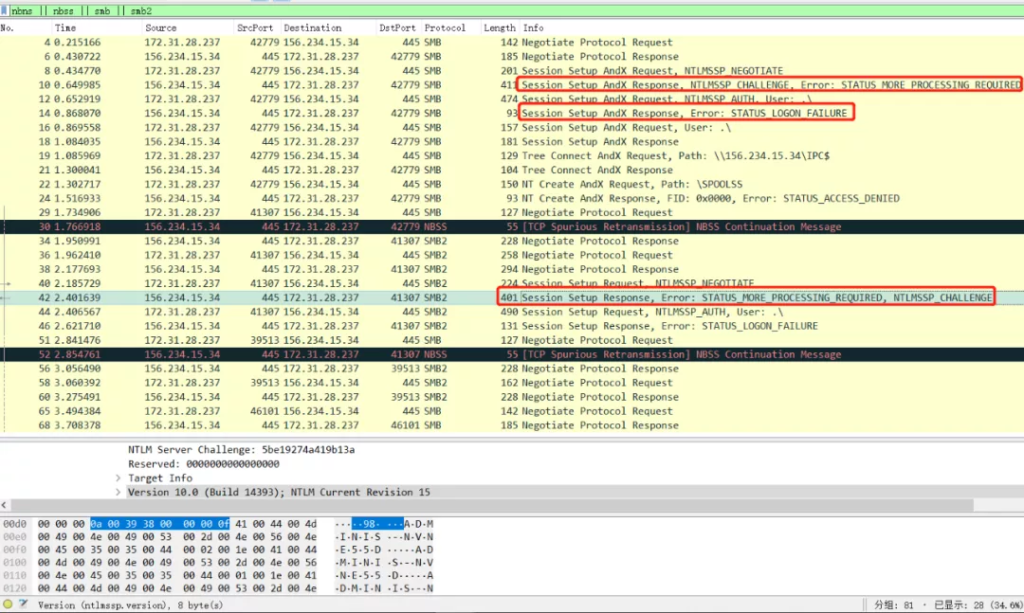
Figure 5: MSF SMBv1 Detection