Traditional vulnerability management approaches can no longer keep up with today’s dynamically changing business needs and attack surfaces that are expanding across clouds, remote workers, IoT, and mobile users. Ad hoc measures, emergency patches, and even comprehensive asset and vulnerability inventory management programs need to evolve into multi-functional security strategies. This layered security needs to include prevention controls and robust detection and response.
Continuous Threat Exposure Management (CTEM) programs with automated pentesting and red teaming, when combined with External Attack Surface Management (EASM), enables a strong cybersecurity posture. These management approaches effectively identify and manage external-facing digital assets, and the security technology andprocesses that discover vulnerabilities to protect those assets.
Protection of digital business assets requires the ability to prepare for threats. This means using a cohesive risk reduction strategy on a regular and repeatable basis. A comprehensive strategy should expose and address a broad array of known and unknown threats and identify vulnerable security gaps from misconfigurations, software faults, and even minor network changes that can create new vulnerabilities.
Best practices are all about applying lessons learned before going into production. A best practice recommends the optimal way of doing things, while pentesting informs security teams of the implementation correctness. When organizations combine testing to discover, fix and validate, with a standard of best practices, security risk is minimized.
Ridge Security auto pentesting, red teaming, and external attack surface management
By implementing auto pentesting, red teaming and EASM security measures, organizations gain greater visibility and control to overcome breaches, minimize risks, and increase security resilience.
Ridge Security’s RidgeBot®, an automated pentest robot for risk-based vulnerability management, acts like human attackers using sophisticated exploits. RidgeBot relentlessly locates exploits across an enterprise network and documents its findings. RidgeBot continuously measures results and effectiveness and verifies vulnerabilities.
RidgeBot enables organizations to conduct automated pentesting from an attacker’s point of view. Before an exposure is even put into production, it can find, assess, prioritize, and fix a wide set of exposures that attackers would see. The resulting validation allows organizations to see what would happen in the event of an attack, how their defenses would cope, and how well the processes would perform. This validation is achieved through breach and attack simulation and automated penetration testing.
RidgeBot in action
The two dashboard screens are RidgeBot Attack Surface Tables. These are pre-defined templates in which RidgeBot identifies a target machine’s OS type, open ports, and active services. They also identify website domain names, sub-domain names, encryption key, web framework and external URL/URI exposures. These tests do not incur a license fee to run, once RidgeBot is installed.
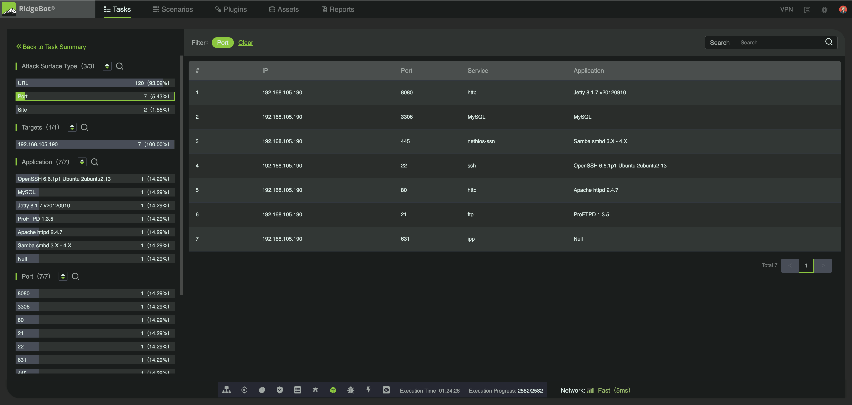
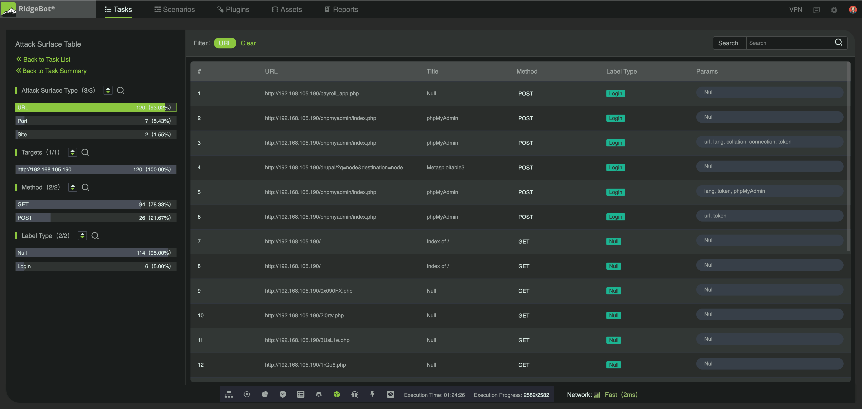
The dashboard screen below shows the pre-defined test scenarios built within RidgeBot. The “Attack Surface Identification” test is included within other test scenarios, with a list of all open ports and active services for servers and externally exposed URLs/URIs. This table is located on the GUI, as well as in the report that can be generated in .csv, .pdf and .html formats.
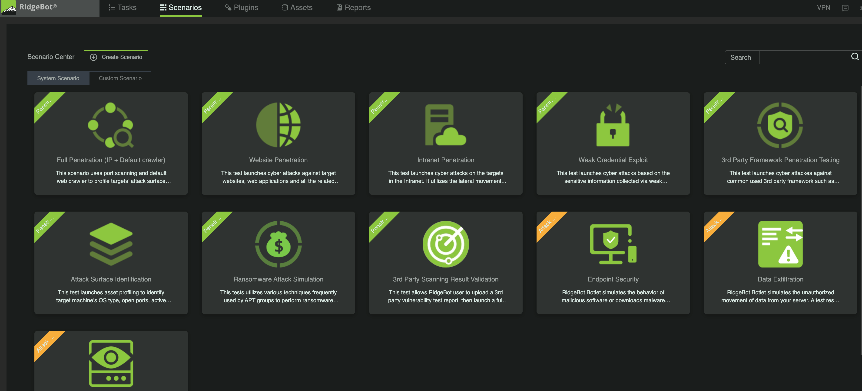
RidgeBot scans, exploits, and validates vulnerabilities, and reports with hard evidence. This enables security and risk teams to identify and manage their digital assets and ensure the technology and processes protecting those assets are reliable and resilient to eliminate risks and vulnerabilities.