Security teams face an ongoing battle in the fight to stay ahead of potential threats in a constantly evolving cybersecurity landscape. Even the most secure systems can hold weaknesses that bad actors may discover and exploit.
To keep organizations secure, the latest RidgeBot update incorporates protections against several new critical CVEs, including MOVEit (CVE-2023-34362) and Apache Superset (CVE-2023-27524). We discussed the MOVEit vulnerability in a previous blog. In this post, we’ll delve into the Apache Superset vulnerability. Apache Superset’s vulnerability, discovered in April, stems from an insecure default configuration in the open-source business intelligence application.
The session validation vulnerability attacks Apache Superset versions up to and including 2.0.1. Installations that haven’t altered the default configured SECRET_KEY allow attackers to authenticate and access unauthorized resources. This capability can enable hackers to harvest credentials and conduct remote code execution.
The screenshots below show RidgeBot discovering the Apache Superset vulnerability, including validation, attack logs and exploit evidence.
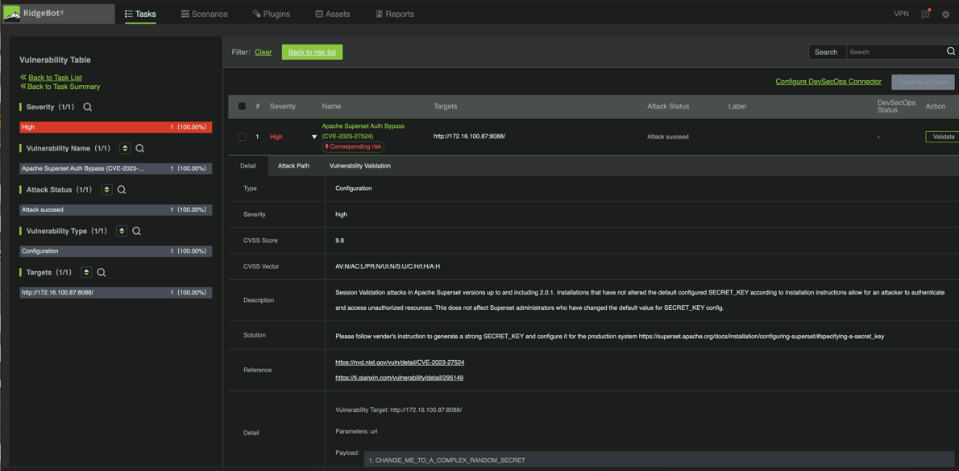
Figure 1: Apache Superset Vulnerability Detected by RidgeBot
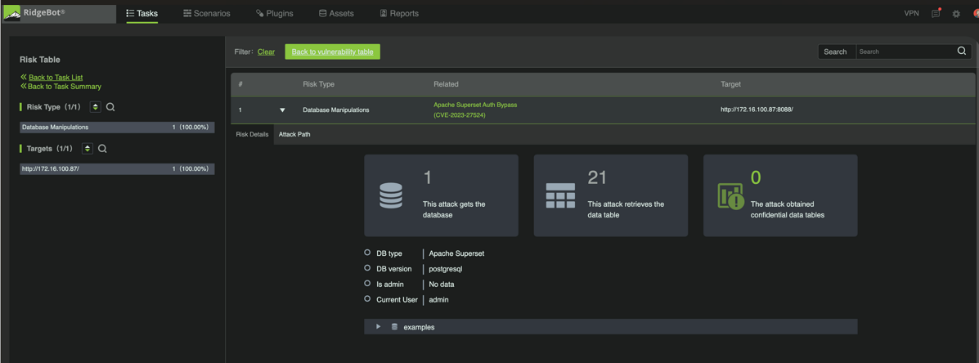
Figure 2: Evidence that RidgeBot successfully exploited Apache Superset.
Seven new plugins for critical CVE exploits
To address newly discovered CVEs, RidgeBot has added new Application Library Scan and Exploit Library plugins to the RidgeBot 4.2.4 release:
New Application Library Scan Plugins 4.43-4.44
- MOVEit Transfer SQLi Vulnerability Exploit(CVE-2023-34362)
- Apache Commons Text Text4shell Command Injection (CVE-2022-42889)
- Apache Superset Auth Bypass (CVE-2023-27524)
New Exploit Library Plugins 4.43-4.44
- MOVEit Transfer SQLi Vulnerability Exploit (CVE-2023-34362)
- VMware ESXi OpenSLP Remote Code Execution (CVE-2020-3992/CVE-2021-21974)
- Apache Commons Text Text4shell Command Injection Exploit (CVE-2022-42889)
- Apache Superset Auth Bypass Exploit (CVE-2023-27524)
If your organization has concerns about any of the mentioned CVEs, please click here to contact us.
RidgeBot’s continuous, automated, and AI-powered pentesting
RidgeBot’s automated penetration testing helps organizations find and fix weaknesses, vulnerabilities, and exposures in their digital assets by testing the network whenever there are changes, additions, updates, or new users. Using collective threat intelligence, vulnerability insights, and AI-powered decision-making to mimic an actual attacker, RidgeBot follows the latest attack methods to find, exploit, and document its findings.
RidgeBot reveals attack paths, confirms vulnerabilities, and gives practical suggestions for fixing vulnerabilities before hackers exploit them. The continuous, automated testing enables defenders to proactively strengthen the security layer across every aspect of their digital domain. And it’s simple to use without requiring highly skilled staff.