API security is a critical aspect of modern web application protection. Even a minor change in a URL parameter can open the door for attackers, potentially exposing sensitive data, leading to breaches, unauthorized access, or service disruptions. OWASP API Security Top 10 outlines the most critical vulnerabilities that organizations must address to secure their APIs effectively. Tackling these risks is essential—and this is where RidgeBot’s Web API Penetration Testing becomes helpful.
What Is Web API Penetration Testing?
Web API penetration testing simulates external attacks on web APIs, making it particularly effective for uncovering hidden vulnerabilities and assessing how far an attacker could penetrate from publicly accessible endpoints. At its core, this process involves evaluating APIs to ensure they operate securely and function as intended. It includes identifying vulnerable endpoints, assessing API behavior for potential issues, preventing sensitive information leakage, verifying the correct implementation of authentication mechanisms, and ensuring that security standards are strong and up to date.
Why Is Web API Testing Important?
Failing to secure these endpoints can lead to serious risks. Broken authorization vulnerabilities may allow unauthorized users to access sensitive data or perform unauthorized actions, resulting in data breaches or resource misuse. Additionally, APIs that expose excessive or sensitive information due to misconfigurations can become prime targets for attackers, leading to severe data leaks. Insufficient security measures may also prevent organizations from detecting and responding to threats in real time, leaving systems vulnerable to exploitation and service disruptions. Given that APIs expose backend systems to external networks, robust Web API penetration testing is essential to safeguard APIs and ensure they remain secure and reliable.
How to Protect Against API Threats?
Introducing RidgeBot 5.0, the Web API Penetration Testing scenario offers advanced features to identify and exploit potential API vulnerabilities in a controlled environment. RidgeBot facilitates both black-box testing, where no credentials are provided, and gray-box testing, which mimics an attacker with partial authenticated access. By detecting reachable API endpoints, RidgeBot uncovers OWASP Top 10 API vulnerabilities, helping to identify risks such as broken authorization that could be exploited by attackers.
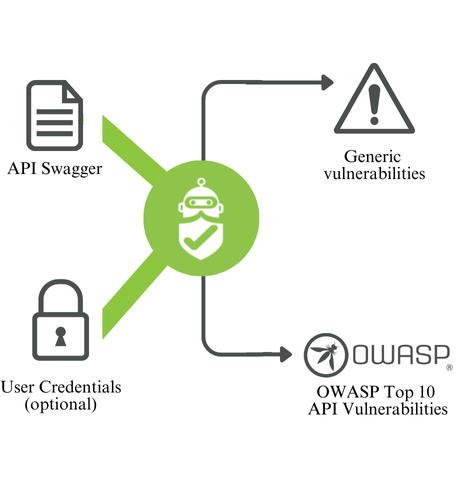
RidgeBot conducts Web API penetration testing through a structured, multi-step approach:
Preparation
The Web API testing starts by providing RidgeBot with API documentation (e.g., Swagger file) to identify endpoints within scope. Account credentials can be supplied for gray-box testing, simulating scenarios where the attacker has limited credentials.
Reconnaissance and Initial Access
RidgeBot performs reconnaissance, examining both documented and undiscovered API endpoints by sending HTTP requests and analyzing responses. This step validates existing security measures and gathers data for future attacks.
Web API Vulnerability Assessment
RidgeBot identifies vulnerabilities from the OWASP API Top 10 by fuzzing inputs, testing for broken access controls, and exploiting business logic flaws. It also performs authorization tests to detect whether users can access unauthorized resources or functions. Besides, RidgeBot will also check generic web vulnerabilities for deeper analysis of your security posture.
Reporting
RidgeBot generates a detailed report outlining the discovered endpoints, vulnerabilities, and exploit details, helping users prioritize and remediate security issues.
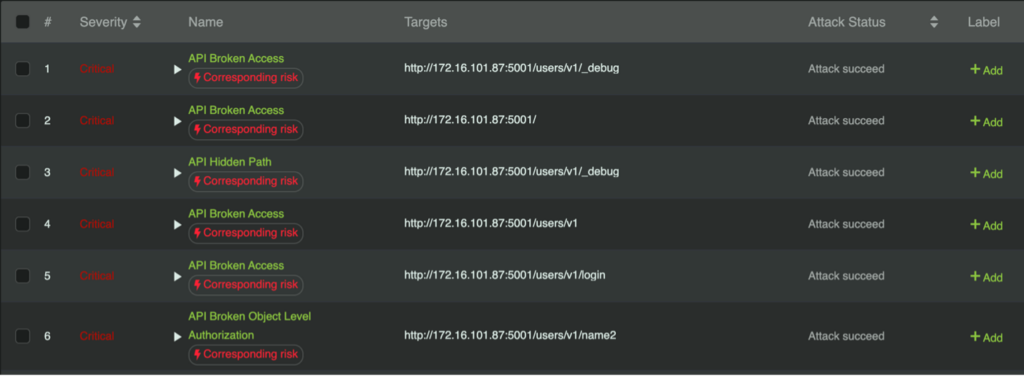
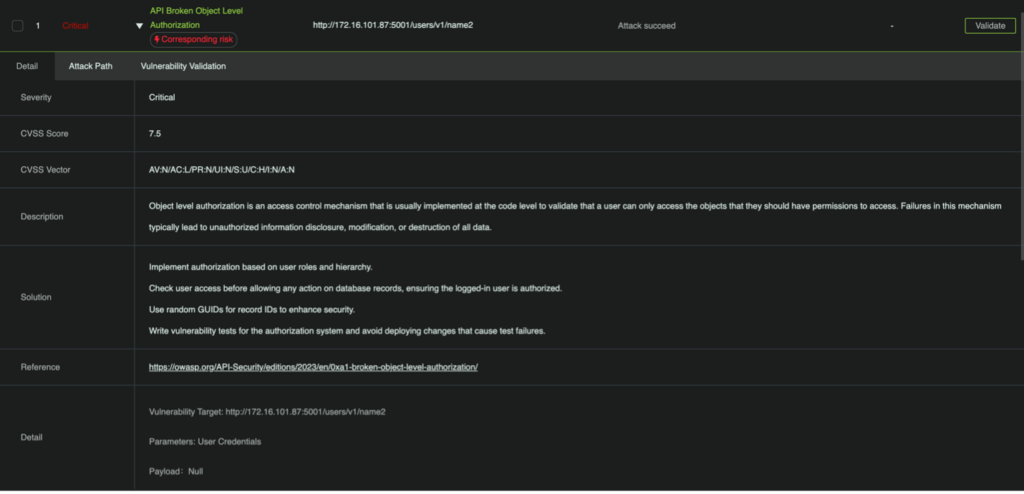
In today’s digital landscape, securing Web APIs is more critical than ever as they are gateways to sensitive data and essential functions within an organization. RidgeBot 5.0 offers a comprehensive solution for identifying and addressing API vulnerabilities, ensuring that your APIs remain protected against the latest threats.
Don’t leave your API security to chance—watch the demo video of our new API pentesting feature to see RidgeBot 5.0 in action or learn how it can enhance your API security strategy with a personalized demo.