The Cybersecurity & Infrastructure Security Agency (CISA) leads the U.S. effort to understand, manage, and reduce risk to cyber and physical infrastructure. In concert with other agencies, they publish a list of the top vulnerabilities that are routinely exploited worldwide. The other agencies include the Australian Cyber Security Center (ACSC), the United Kingdom’s National Cyber Security Center (NCSC), and the U.S. Federal Bureau of Investigation (FBI).
Ridge Security pays close attention to these vulnerabilities because cyber actors readily exploit newly disclosed vulnerabilities. In 2021, cyber actors continued to exploit perimeter-type devices that support remote work options, such as virtual private networks (VPNs) and cloud-based environments. Many VPN gateway devices remain unpatched because the growth of remote work options is challenging the ability of organizations to keep pace with routine software patching.
The majority of vulnerabilities being exploited today were disclosed during the past two to three years or even longer. Among the most highly exploited vulnerabilities is CVE-2019-19781 which is a critical vulnerability in Citrix’s Application Delivery Controller (ADC) Remote Code Execution (RCE) – a load balancing application for web, application, and database servers. RidgeBot will detect this vulnerability. Other highly exploited vulnerabilities include Microsoft, Pulse, Atlassian, Drupal, and Fortinet. Most of these vulnerabilities allow remote code execution.
Ridge Security takes a two-step approach to vulnerabilities. First, we insure that we can detect and report on them. Second, we learn how to exploit them. Of the top ten routinely exploited CVEs in 2020 RidgeBot can detect 5 of them and can exploit one of them. The CVEs we can detect include Citrix ADC Remote Code Execution (CVE-2019-19781), Zerologon – Windows Netlogon Elevation of Privilege (CVE-2020-1472), Microsoft SharePoint Remote Code Execution (CVE-2019-0594 / CVE-2019—0604), Atlassian Crowd Unauthenticated Code Execution (CVE-2019-11580) and Drupal remote code execution (CVE-2018-7600), which we can detect and exploit.
Organizations are encouraged to update software versions as soon as possible after patches are available. If this is not possible consider applying temporary workarounds or other mitigations, if provided by the vendor. If an organization is unable to update all software shortly after a patch is released, at least prioritize patching the CVEs that are known to be exploited to the largest number of potential attackers, such as internet-facing systems. And, always consider running RidgeBot since it provides insight into your cybersecurity landscape.
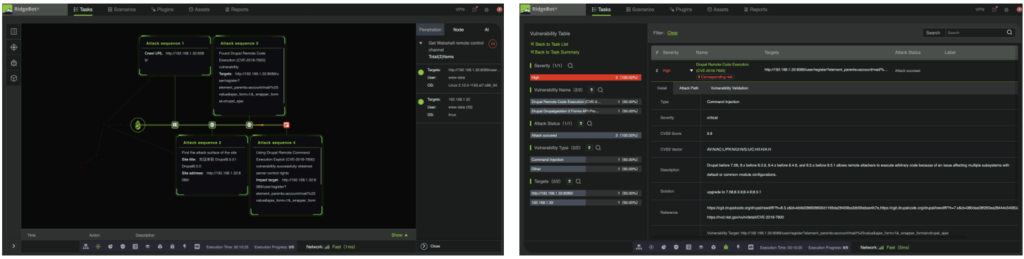
Figure 1: Attack sequences to exploit Drupal RCE CVE-2018-7600, and Detected by RidgBot
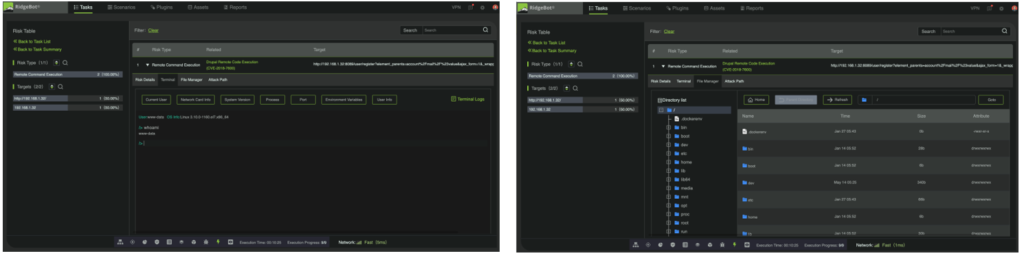
Figure 2: Shell control and File StructureObtained by a successful exploit of Drupal RCE CVE-2018-7600
