Overview of RidgeBot’s Automated Penetration Testing Tool
Eliminate false-positive vulnerabilities
Penetration testing plays an important role in an organizations’ ability to identify exposures, vulnerabilities and weaknesses in their cyber defenses. Many organizations only test annually or on an ad hoc basis. They rarely conduct the manual testing process more frequently, as they typically don’t have the technology, time, and resources to continuously test their environments.
However, automated penetration testing allows organizations to close the windows of opportunity for hackers, by continuously running tests whenever there is a network change, device configuration change, new application release, and allocation of new user groups.
Internal Attack
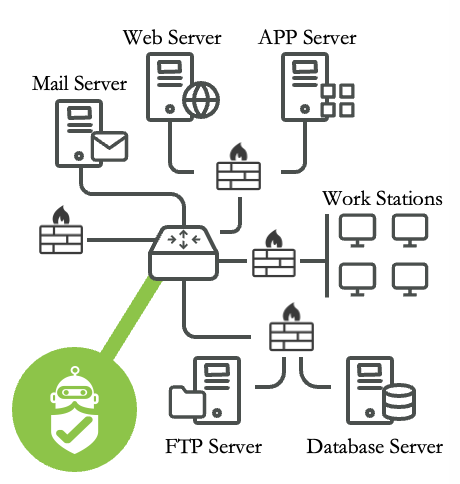
External Attack
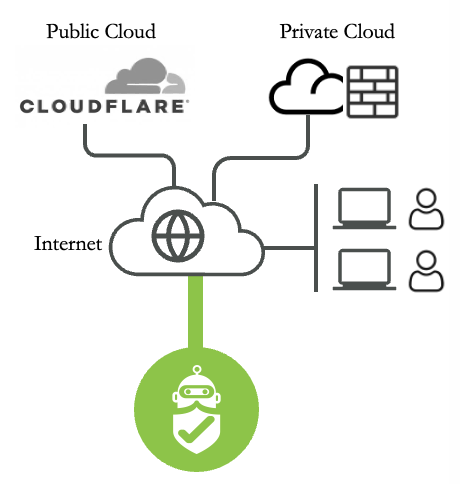
Authenticated Penetration
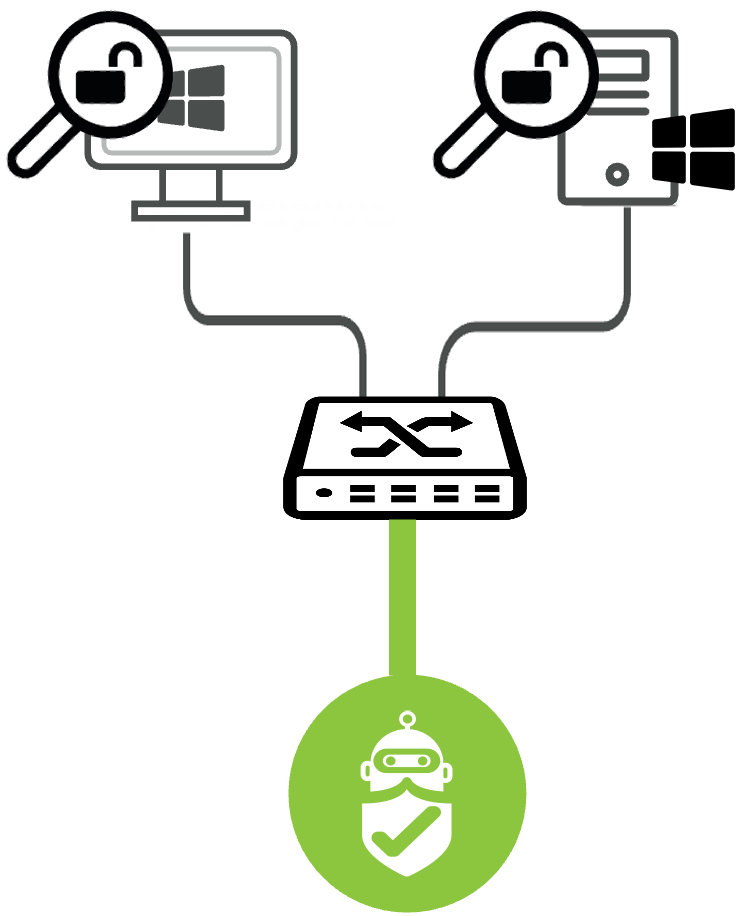
Lateral Movement
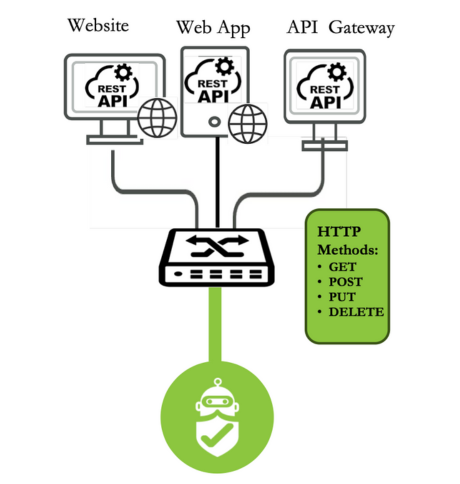
Web API

Built for enterprise environments — works for any size business
Six Features Differentiate RidgeBot®
Smart Fingerprinting and Smart Web Crawling
RidgeBot® automatically crawls or scans the specified IT infrastructure to identify and document a broad type of assets and the attack surfaces of those assets
- 5600+ OS fingerprints/11000+ Service fingerprints
- Asset Types Supported: IPs, Domains, Hosts, OS, Apps, Websites, Plugins, Network and IoT Devices
The following technologies but not limited to are included in this stage:
- Crawling, URL brute force, domain name resolution, subdomain brute-force, associated domain extraction, neighboring site inspection, web fingerprint, host fingerprint, system fingerprint, active host inspection, email extraction, login entries discovery
Support all major web frameworks
- WordPress
- PHP/SQL
- VUE/React
- JavaScript
RidgeBrain Expert Model and Vulnerability Mining
By leveraging the Asset Profiling results, RidgeBot® will examine the assets and attack surfaces against its vulnerability knowledge base, discover all potential vulnerabilities to exploit:
- Web Applications
- Host/Database Servers
- Weak Credentials
- 3rd Party Framework vulnerabilities
The following techniques are used during the vulnerability mining process:
- Weakness discovering: Identify possible weak links on the attack surface and check for vulnerabilities based on the intelligent decision system such as the expert models and RidgeBot® brains.
- Vulnerability scanning: Access and test the target system by using packet generated by an automatic tool and the payload provided by the attack component, vector engine etc., and the returned results are checked to determine whether there are vulnerabilities that can be exploited.
Auto Exploitation
RidgeBot® has an extensive knowledge base, the customer can either choose the exploits based on the test goal and target; or choose to use full scan and have RidgeBot® conduct auto-exploitation.
- 2B+ threat intelligence
- 150K+ exploit database
- 6000+ build-in POC exploits
The following techniques are used during the vulnerability exploit process:
- Internal attack: Launch attacks from inside of Enterprise network with customer’s permission, focusing on exploiting vulnerabilities discovered on local network and systems.
- External attack: Launch attacks from outside Enterprise networks towards publicly accessible assets such as organizations’ websites, file shares, or services hosted in public cloud/CDN
- Lateral Movement: After gaining a permission to the target host, use the host as a pivot to further exploit vulnerabilities and gain access to other parts of the system.
Realtime Attack Action Visualization
Auto Topology Drawing
- Shows relationships of assets and attack surfaces
- Map out vulnerabilities and risks
Full Attack Path Visibility
- Track the attack source and show the attack details
Show the real-time actions on the dashboard
- Discover
- Scan
- Exploit
Risk-based Assessment
Health Score: Rank and remediate vulnerabilities based on risk assessment
- Detailed and specific ranking of the most harmful vulnerabilities
- Visualize the kill-chain
- Comprehensive health score based on the weighted evaluation
Kill Chain Visualization: A Risk is defined as “An exploit with a completed kill-chain accomplished”
- Exploit attempts launched toward each exploitable vulnerability, only those accomplished the whole kill-chain will be documented in the final report.
- Four types of risks shown in the final report
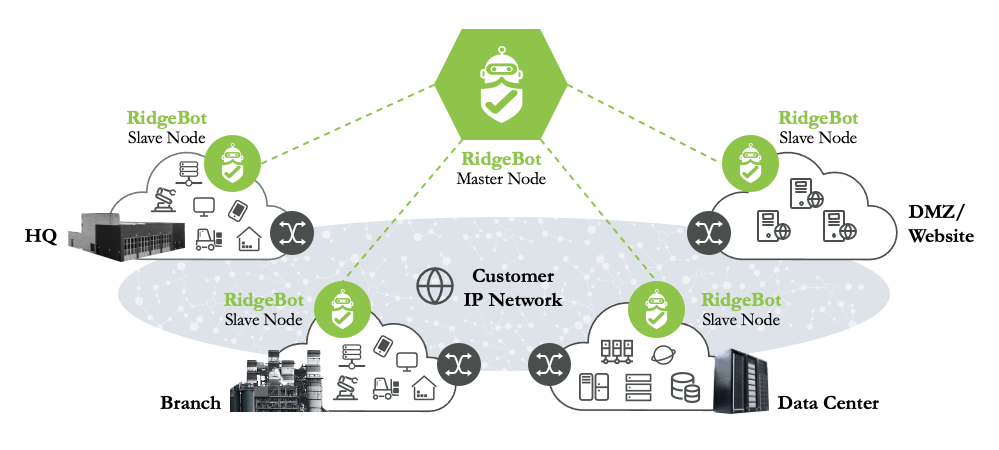
Distributed Architecture for Large Scale Infrastructure
Recommendation: One RidgeBot® Slave Node per 500 target systems (or per subnet)
- Smart Fingerprinting and Smart Web Crawling
- RidgeBrain Expert Model and Vulnerability Mining
- Auto Exploitation
- Realtime Attack Action Visualization
- Risk-based Assessment
- Distributed Architecture for Large Scale Infrastructure
RidgeBot® automatically crawls or scans the specified IT infrastructure to identify and document a broad type of assets and the attack surfaces of those assets
- 5600+ OS fingerprints/11000+ Service fingerprints
- Asset Types Supported: IPs, Domains, Hosts, OS, Apps, Websites, Plugins, Network and IoT Devices
The following technologies but not limited to are included in this stage:
- Crawling, URL brute force, domain name resolution, subdomain brute-force, associated domain extraction, neighboring site inspection, web fingerprint, host fingerprint, system fingerprint, active host inspection, email extraction, login entries discovery
Support all major web frameworks
- WordPress
- PHP/SQL
- VUE/React
- JavaScript
By leveraging the Asset Profiling results, RidgeBot® will examine the assets and attack surfaces against its vulnerability knowledge base, discover all potential vulnerabilities to exploit:
- Web Applications
- Host/Database Servers
- Weak Credentials
- 3rd Party Framework vulnerabilities
The following techniques are used during the vulnerability mining process:
- Weakness discovering: Identify possible weak links on the attack surface and check for vulnerabilities based on the intelligent decision system such as the expert models and RidgeBot® brains.
- Vulnerability scanning: Access and test the target system by using packet generated by an automatic tool and the payload provided by the attack component, vector engine etc., and the returned results are checked to determine whether there are vulnerabilities that can be exploited.
RidgeBot® has an extensive knowledge base, the customer can either choose the exploits based on the test goal and target; or choose to use full scan and have RidgeBot® conduct auto-exploitation.
- 2B+ threat intelligence
- 150K+ exploit database
- 6000+ build-in POC exploits
The following techniques are used during the vulnerability exploit process:
- Internal attack: Launch attacks from inside of Enterprise network with customer’s permission, focusing on exploiting vulnerabilities discovered on local network and systems.
- External attack: Launch attacks from outside Enterprise networks towards publicly accessible assets such as organizations’ websites, file shares, or services hosted in public cloud/CDN
- Lateral Movement: After gaining a permission to the target host, use the host as a pivot to further exploit vulnerabilities and gain access to other parts of the system.
Auto Topology Drawing
- Shows relationships of assets and attack surfaces
- Map out vulnerabilities and risks
Full Attack Path Visibility
- Track the attack source and show the attack details
Show the real-time actions on the dashboard
- Discover
- Scan
- Exploit
Health Score: Rank and remediate vulnerabilities based on risk assessment
- Detailed and specific ranking of the most harmful vulnerabilities
- Visualize the kill-chain
- Comprehensive health score based on the weighted evaluation
Kill Chain Visualization: A Risk is defined as “An exploit with a completed kill-chain accomplished”
- Exploit attempts launched toward each exploitable vulnerability, only those accomplished the whole kill-chain will be documented in the final report.
- Four types of risks shown in the final report
Recommendation: One RidgeBot® Slave Node per 500 target systems (or per subnet)
With RidgeBot® enterprises gain an attacker’s perspective—before real hackers do.
While basic vulnerability scanners and one-step exploitation tools leave critical gaps, RidgeBot® goes further—mimicking real-world attacker behavior with post-exploitation validation. This capability reinforces its position as the most advanced risk-based vulnerability management platform available.
How RidgeBot® Works Like a Real Attacker
- Escalates privileges and deploys a lightweight Botlet on compromised systems.
- Acts as an internal pivot, probing deeper into class C segments—or even across networks (if dual-NIC systems are breached).
Why Organizations Need This Capability
- Uncover hidden risks—validate lateral movement paths deep inside networks.
- Stay ahead of APTs & ransomware—test defenses against real-world attack chains.
- Control testing scope—adjust post-exploitation depth to match security policies.
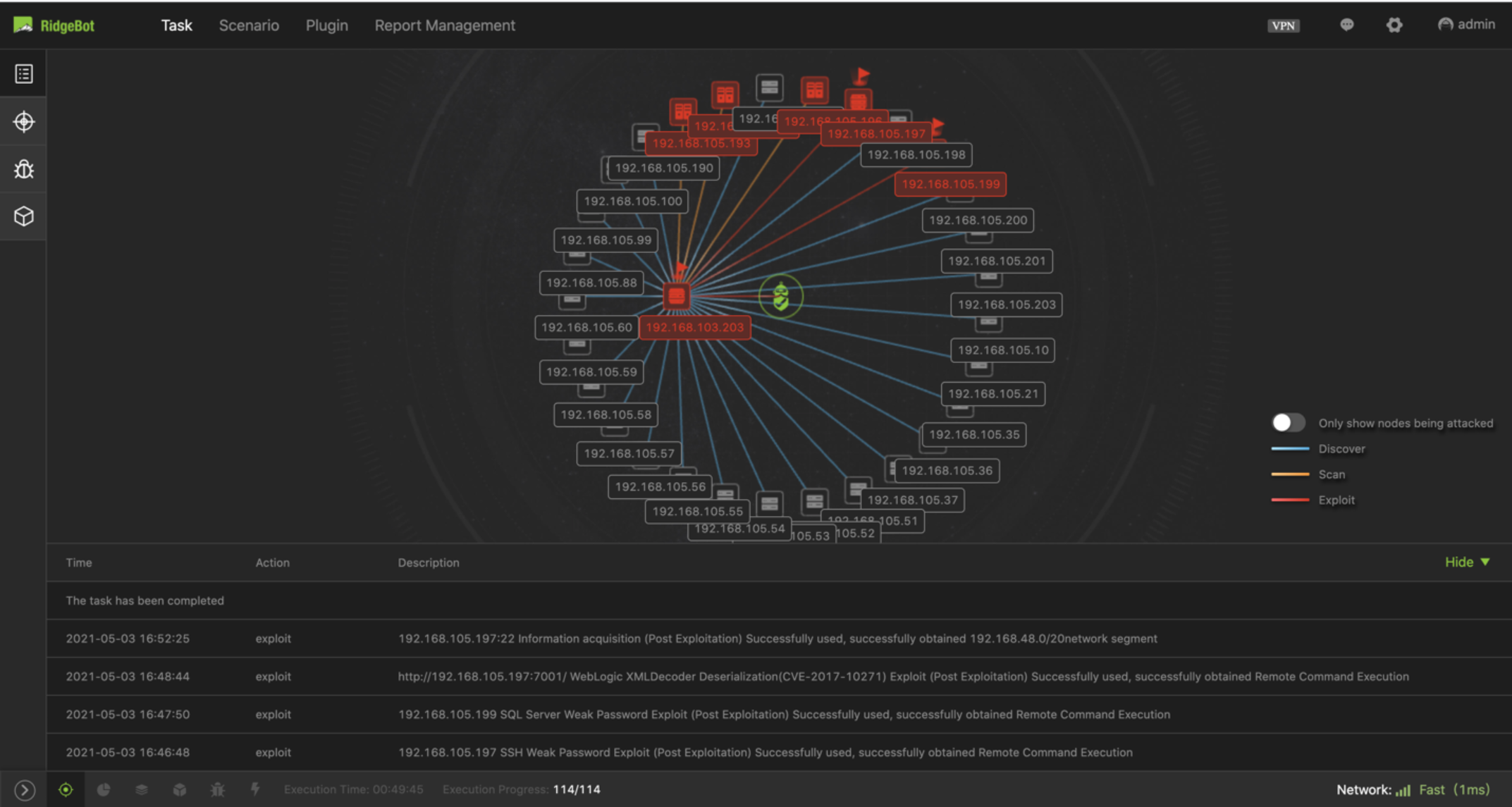
Figure 1. This node view shows that RidgeBot® is making lateral movement from network segment 103 to 105.
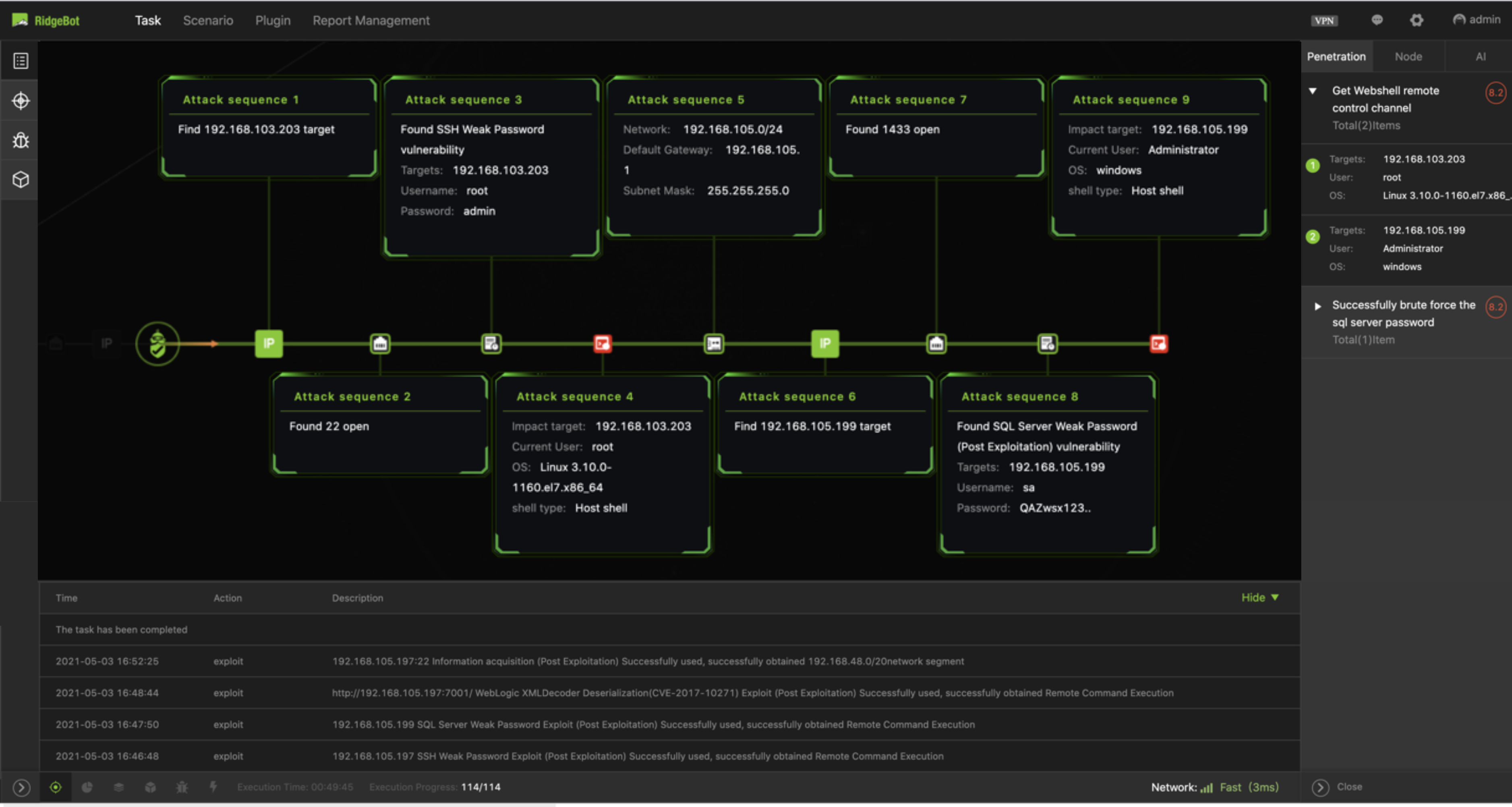
Figure 2. The attack sequences illustrate the RidgeBot’s® kill chain actions.
Request a Demo of RidgeBot®
Learn first hand how RidgeBot® can make the lateral movement.
Four ways to learn about RidgeBot®
Helpful Resources


View a sample RidgeBot business risk-based security report.
FAQ’s – RidgeBot® AI Agent for Autonomous Penetration Testing
What is autonomous penetration testing?
Autonomous penetration testing uses software to continuously test your network for vulnerabilities. RidgeBot® crawls your systems, identifies assets with smart fingerprinting, discovers weaknesses, and automatically exploits them using real POC exploits without needing security experts.
Is autonomous penetration testing worth it?
Yes. Autonomous penetration testing runs continuously and finds vulnerabilities 100x faster than manual penetration testing, which only happens once or twice a year. It closes windows of opportunity for hackers by testing whenever your network changes.
What is autonomous penetration testing versus manual penetration testing?
Manual penetration testing requires experienced testers and takes weeks. Autonomous penetration testing with RidgeBot® runs continuously and shows real attacker behavior with complete attack chains. It finds hidden risks that basic vulnerability scanners miss.
How does RidgeBot® perform lateral movement testing?
RidgeBot® exploits vulnerabilities to gain access, then uses that system as a pivot to probe deeper into your network. This lateral movement testing shows how attackers move through your systems after breaking in.
What are RidgeBot's autonomous penetration testing features?
RidgeBot® has six key features: smart fingerprinting identifies assets, vulnerability mining discovers weaknesses, auto exploitation runs 6000+ POC exploits, real-time attack visualization shows the kill chain, risk-based assessment ranks vulnerabilities, and distributed architecture scales for large networks.