Learn how enterprise customers achieve Risk-Based Vulnerability Management using RidgeBot®‘s automated penetration testing technology. These 10 key RidgeBot® features provide an overview showing the RidgeBot® in action. We recommend a product demonstration where you can ask questions specific to your environment and security concerns.
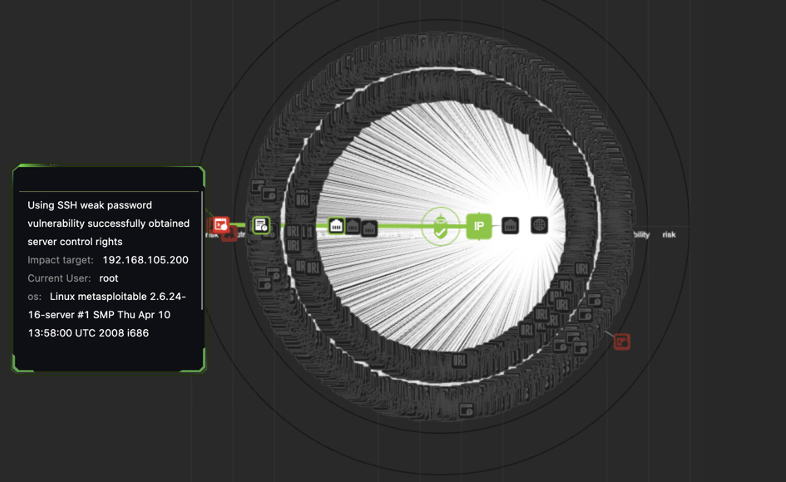
Attack Topology Auto-Drawing
Visualized attack topology and attack path:
- Overall attack situation and details of each attack
- Attack forensic, vulnerability fix and risk mitigation
- Global attack topology with five layers of information
Drill down to the Risk to see the detailed attack path of each attack
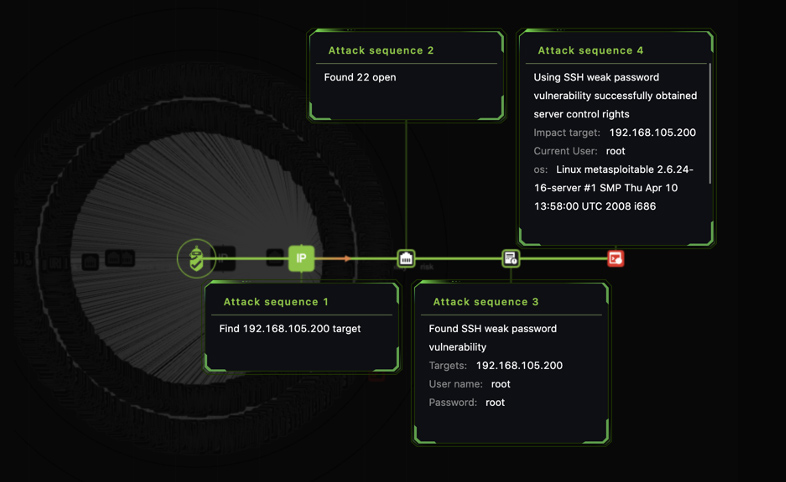
Attack Path Full Visibility
Visualized the process of how a vulnerability is discovered and exploited
- Vulnerability discovery
- Vulnerability exploitation
Five Layers of attack information:
- Attacker: RidgeBot®
- Target: target IP
- Attack surface: found open port
- Vulnerability: vulnerability details with target info.
- Risk: how the vul is used to attack the target system
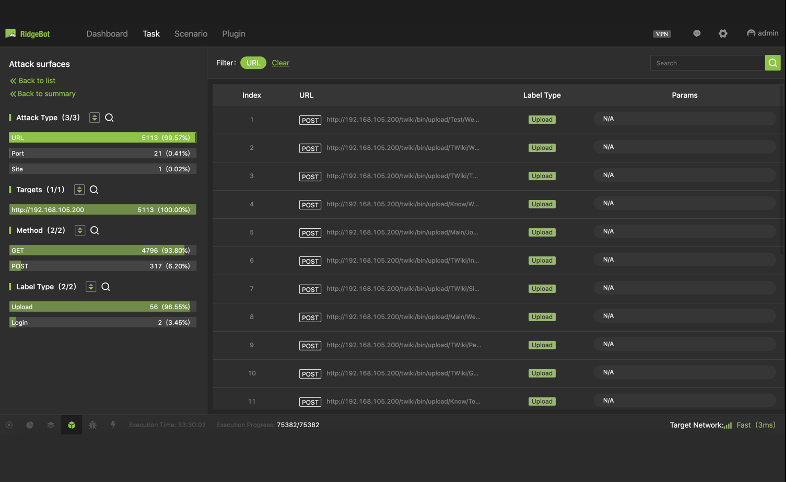
Attack Surface Auto-Discovery
Discover the attack surface for the targets and identify its attack mechanism details in the following categories:
- URL: URL/Domain/method
- Port: IP/App/Port/Service
- Email: email address
- Back-end login entries: URL/Domain/post data/method
- File upload entries: URL/Domain/post data/method
- Neighboring domain: URL/Domain/post data/method
- Front-end entries: URL/Domain/post data/method
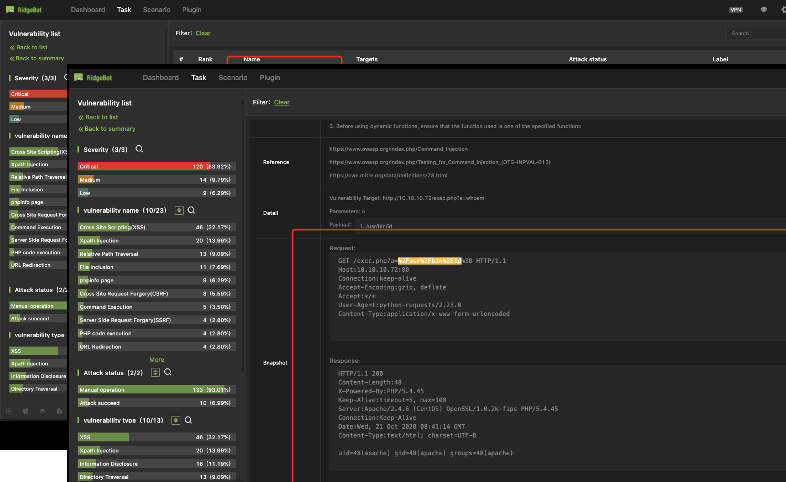
Comprehensive Vulnerability Details
Show the details of each vulnerability including:
- Vulnerability Type
- Severity Rank
- CVSS score/vector
- Description
- Fix Solution
- Reference info.
- Details: payload etc.
- Attack snapshot
Attack snapshot:
- for HTTP request only now, not supported for socket, TCP or UDP
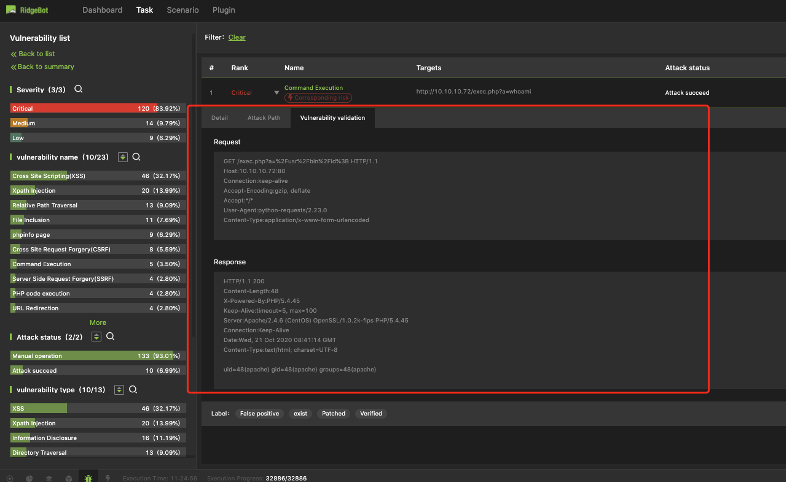
Immediate Web Application Vulnerability Validation
Vulnerability validation is to exploit the vulnerability to validate its existence.
HTTP reload is a typical validation method, its goal is to reload the HTTP request and get the result leveraging the vulnerability
Risk Details
Risk is the result of the vulnerability exploitation and defined as an exploit that accomplishes the whole kill-chain.
RidgeBot® 3.1 supports 4-type of risks:
- Remote Command Execution
- Credential disclosure
- Sensitive information exposure
- Database manipulation
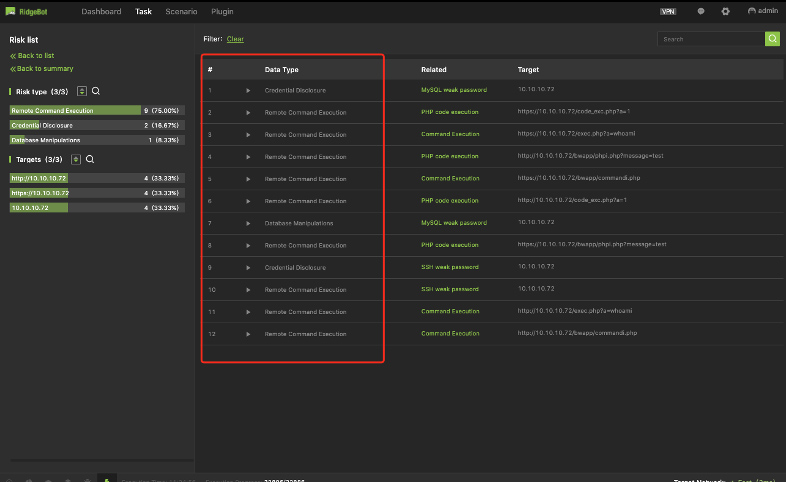
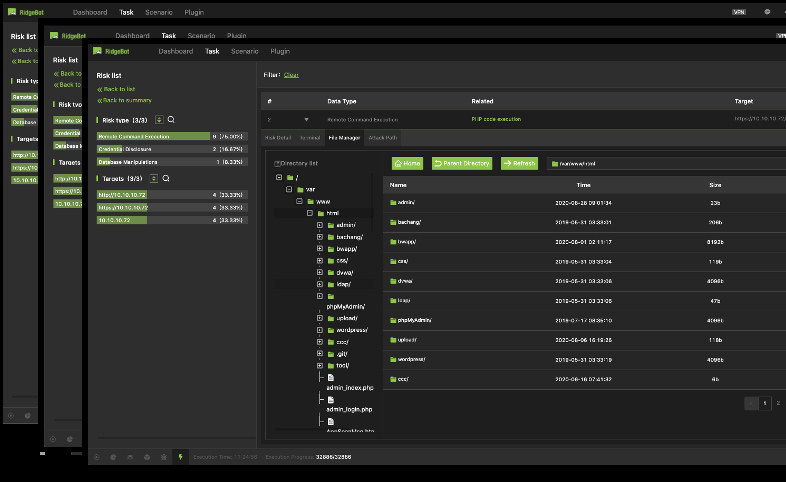
Risk Details with Evidence – Remote Command Execution
Details of Remote Command Execution risk
- Risk details: shell type/path, user, OS etc.
- Terminal: a virtual machine to execute the remote command
- File Manager: the file folder directory on the target system
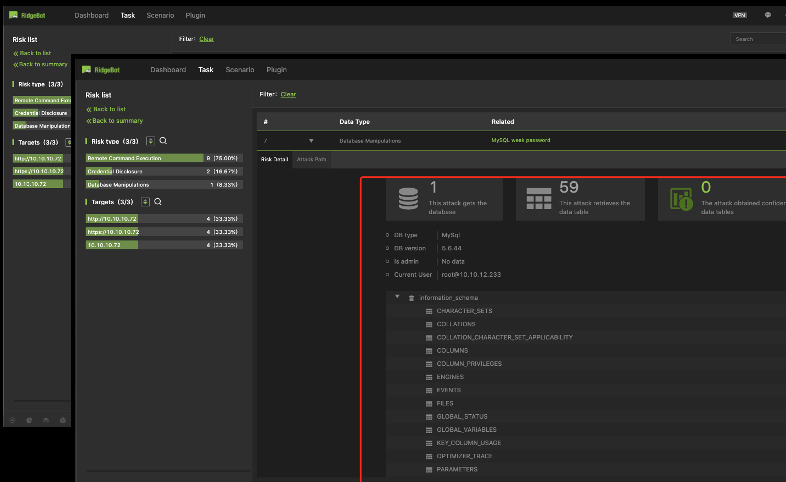
Risk Details with Evidence – Database Manipulation
Details of Database manipulations risk
- Show how the database is manipulated by either Week password or SQL injection
- Can retrieve and show details of the Database library and table as a result of the risk
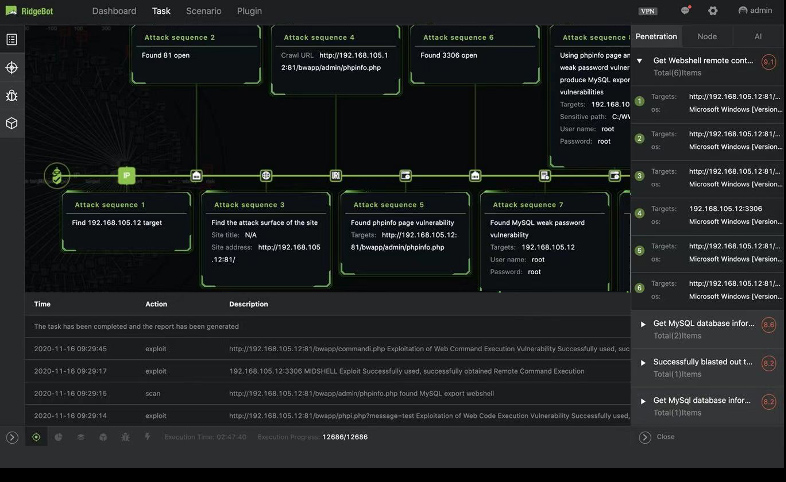
Advanced Attacks: Joint and Iterative Exploitation
Jointly exploit the vulnerabilities to find more risks
- Vulnerability a + vulnerability b
- Vulnerability a + new attack surface
- Vulnerability a + other new information (credentials, privilege escalation)
The iterative attack/exploitation
- A vul or risk result discovered from the previous step can be used again to exploit the system further.
- E.g. leverage the authentication information obtained for further attacks.
- Note: The iteration is for single target only, not for the lateral movement
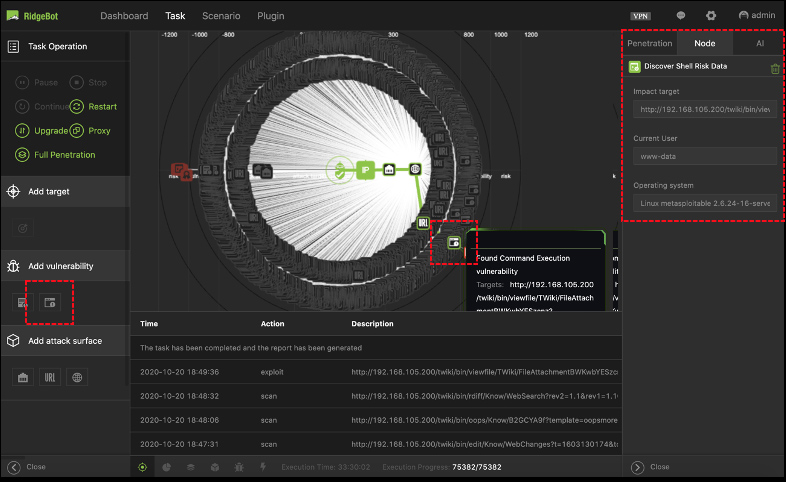
Dynamic Task Configuration
Dynamically update the attack tasks during a test
- Add target, attack surface, vulnerability etc. during the attack process
- The user can add their known vulnerabilities to the iterative tasks for a specific purpose or to improve the attack result.
Experience a live demo
Learn how RidgeBot or RidgeShield can support your security and IT teams.