New! from Ridge Security
RidgeShield Cloud Workload Protection, is your first line of defense, providing zero-trust micro-segmentation technology to protect cloud workloads, regardless of whether they are deployed on-premises, in hybrid cloud, or multi-cloud environments. With RidgeShield, organizations can ensure the security posture of their network against sophisticated security threats.
As an innovative host based micro-segmentation platform, RidgeShield supports a wide range of operating systems and workloads, continuously monitoring traffic across workloads and enforcing unified security policies across any environment.
RidgeShield Key Business Benefits
Request an online demonstration of RidgeShield
Product Demonstration Request an online demonstration of RidgeShield. Learn how your team can easily implement a consistent workload security policy monitoring across on-premises and multi-cloud and test your deployment using the integrated Automated Security Validation platform RidgeBot.
Microsegmentation techniques are also pivotal in stopping and containing intrusion attempts. Forrester’s Trusting Zero Trust study found that 75% of CISO- and director-level leaders consider microsegmentation a key technology foundation for achieving their zero-trust strategic initiatives and are seeing results from their investments. Ponemon Institute’s 2022 report, Managing Risks & Costs At The Edge, found that 54% of organizations have had an average of five attacks on their endpoints in the past year. The annual cost of these annual attacks is $1.8 million or $360,000 per attack. Microsegmentation is proving its value by stopping intrusions and breaches.
RidgeShield Core Functions
Label-based Micro-Segmentation
Provides the ability for the user to define various labels to categorize their assets
Business Orientated FlowView
Enables business-oriented traffic flow view to graphically display the relationship between the micro-segments
Security Best Practice Checks for Workloads
Provides security best practice checks for the workloads, e.g. Windows and Linux workloads
Asset Management
Enables asset management, which a common place to view the workloads, their membership in various micro-segments, and their status
Supporting On-prem, Hybrid & Multi-Cloud Environments
RidgeShield is not limited to Cloud workloads only. It can span on-prem workloads and cloud workloads, i.e. it supports hybrid environment. It also supports multi-cloud environment
Integrated Security Testing
Last but least, RidgeShield has automated security testing integrated

Datasheet Download
Ridge Security Cloud Workload Protection solution
RidgeShield Differentiation
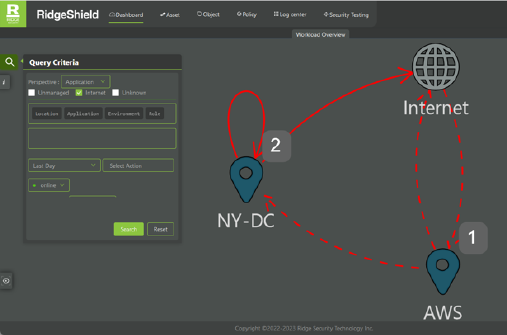
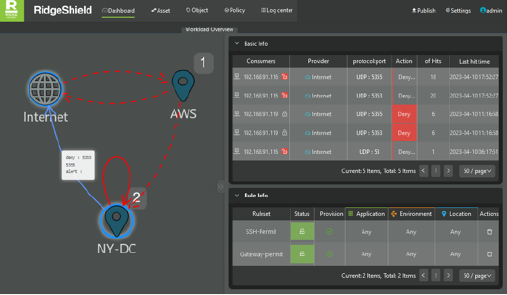
Intelligent Visualization
- Visualize all communication between workloads regardless of location
- Flexible grouping of workloads based on label assignments, in 1-dimensional or multi-dimensional views
- Easy identification of missing or unmanaged assets
- Real-time view change via drag & drop
- Identification of policy violations via color-coded links
Business-centric Security Policy and Automated Policy Enforcement
- High-level business-centric security policies
- Consistent security policy across on-prem, hybrid and multi-cloud environments
- Easy creation of rules between workloads by clicking the link
- Automatic enforcement of defined policies in real time
- Order independent security policies unlike traditional firewalls
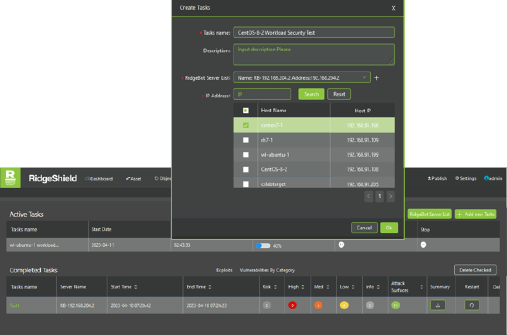
Integrated with Security Testing
- Single click to start security testing on managed assets
- Security testing includes attack surface discovery, vulnerability scanning, vulnerability exploit, and mis-configurations
- Integrated with DevOps tools to track and remediate discovered security issues
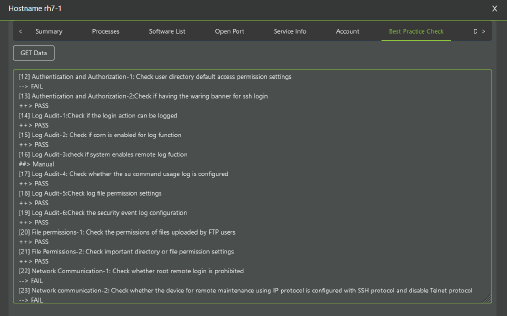
Workload Security Best Practice Checks
RidgeShield provides security best practice check for workloads.
Linux
- Account
- Password policy
- Authentication policy
- Log audit
- Networking
- File system & disk space
Windows
- Account info checking
- Hidden account checking
- Network share checking
- Registry
- Open ports
- File system checking
See RidgeShield in action
Zero-Trust Security with Micro-Segmentation, Automated Security Testing, and Protection