Common vulnerabilities and exposures, or CVEs, are a list of publicly disclosed computer security flaws. They help IT professionals prioritize and address critical vulnerabilities to ensure their systems are protected. MITRE corporation oversees the CVE program, with funding from the Cybersecurity and Infrastructure Security Agency (CISA). CVEs are in other databases, including the U.S. National Vulnerability Database (NVD), the CERT/CC Vulnerability Notes Database, and various lists maintained by security advisories, vendors and researchers.
Recent CVE example
On May 18th, CISA and the Multi-State Information Sharing & Analysis Center (MS-ISAC) released a joint Cybersecurity Advisory in response to active exploitation CVE-2022-1388. This vulnerability was found in F5 Network’s BIG-IP, which can allow unauthenticated actors to gain control of the system through the management port or self-IP addresses.
It’s important for all organizations with these devices to apply the F5 patch, to eliminate this vulnerability that can allow attackers to remotely execute malicious code. This exploit uses two techniques, “admin:” empty token bypass authentication, and “abusing HTTP hop-by-hop request header”, that manipulates the header to enable a remote code execution (RCE) attack.
Cybersecurity risk is comprised of threats, assets and vulnerabilities
Cybersecurity scanners generate thousands of vulnerabilities with each scan, and SIEMs produce tens of thousands of logs with warnings every day. Firewalls are configured with hundreds, and even thousands of policies and rules. Determining which pose real risks, what to prioritize, and how big the impact might be, are challenges CISO’s face on a daily basis.
Penetration testing and red teaming play an important role in an organizations’ ability to identify exposures, vulnerabilities and weaknesses in their cyber defenses. Many organizations only test annually or on an ad hoc basis. They rarely conduct the manual testing process more frequently, as they typically don’t have the technology, time, and resources to continuously test their environments. However, automated pen testing allows organizations and MSSPs to close the windows of opportunity for hackers, by continuously running tests whenever there is a network change, device configuration change, new application release, and allocation of new user groups.
RidgeBot quickly assesses your infrastructure, identifying vulnerabilities
The goal of traditional scanners is to find as many vulnerabilities as possible. But according to statistics, only 3% of all vulnerabilities are exploitable. Within a typical environment, the majority are actually harmless. When security teams respond to CVEs found “in the wild”, the actual risk may not have a direct or significant impact. They need only be concerned about critical vulnerabilities that actually exist within their environment. Otherwise, they become consumed with, and distracted by:
- High false-positives
- Patch priorities not based on a real attack possibility
- No verification and validation of vulnerabilities
- No real PoC exploit
This is why it’s critically important for organizations to have multi-layered security, and best practice-based security protocols and procedures. Deploying automated penetration testing within the enterprise network removes CVE risk. RidgeBot’s continuous automated pen testing will discover and protect against new and unknown CVEs, like CVE-2022-1388.
For every CVE, RidgeBot has two types of Plugins. Detection – verifies if the vulnerability exists within the environment; and Exploit – launches a payload to the threat in order to trigger a vulnerability. For CVE-2022-1388, RidgeBot scanned and discovered the exploit, and within a few days released a proof-of-concept, or PoC, with Plugin Lib 3.41.1, that was added to the RidgeBot database. RidgeBot users can now run automated pen testing against their infrastructure with F5 BIG-IP devices, execute exploits, and produce a report, complete with evidentiary findings.
The dashboard screen below shows the result of RidgeBot detecting and exploiting the F5 BIG-IP device’s root access. The evidence shows an unauthorized RCE (Remote Command Execution) on a specific target IP address. The risk type (RCP) was 100%, and the target IP identified was 100% compromised.
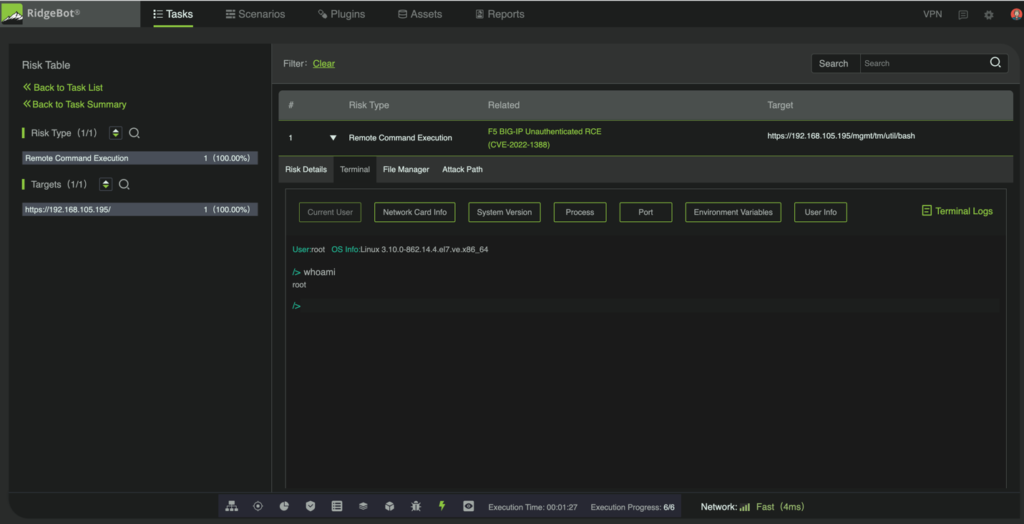
Exploitation result: Gained affected system’s root access
Security teams are always trying to stay one step ahead of bad actors. Unfortunately, their advisories don’t follow their playbook. And no matter how well-defended systems are, security protections are never perfect. A hacker only needs one vulnerability to be successful. Vulnerability Assessment and Penetration Testing (VAPT) represents a broad range of security assessment services that identify and help address cybersecurity exposures across an organization’s IT estate. However, risks can’t be eliminated by only scanning. That’s why RidgeBot scans, exploits and validates vulnerabilities, and reports with hard evidence.
