Oracle WebLogic is an enterprise Java management platform which is used to manage, deploy, and distribute large-scale Java applications. It is used both for on-premise and cloud deployment and management. It facilitates the communication between distributed services and helps ease the pains of dealing with large-scale distributed systems.
This year a vulnerability, labeled CVE-2023-21839, was found in Oracle WebLogic that allows unauthenticated attackers the ability to load and run arbitrary code on the host server. We will cover some of the core concepts that are in use to make this vulnerability possible as well as how RidgeBot detects and exploits the vulnerability.
To exploit this vulnerability, there are a couple of services we must set up on our side. We first will startup our own LDAP server which will host a malicious Java file for the WebLogic server to receive. LDAP servers are meant to host directory information for a service. In this case it will hold a Java object that WebLogic will use to obtain directory information, which will cause our exploit code to be run. We will also set up our own remote listener, which will be used to issue commands to the host machine once we have gained access to the server.
For our target to run the malicious code, we need to tell it about the LDAP server and get it to perform a directory look up. This request is done using a special protocol that WebLogic uses when communicating with the various services it manages. After we communicate with it over this protocol, WebLogic will then receive the malicious Java code from our LDAP server, which will then be executed.
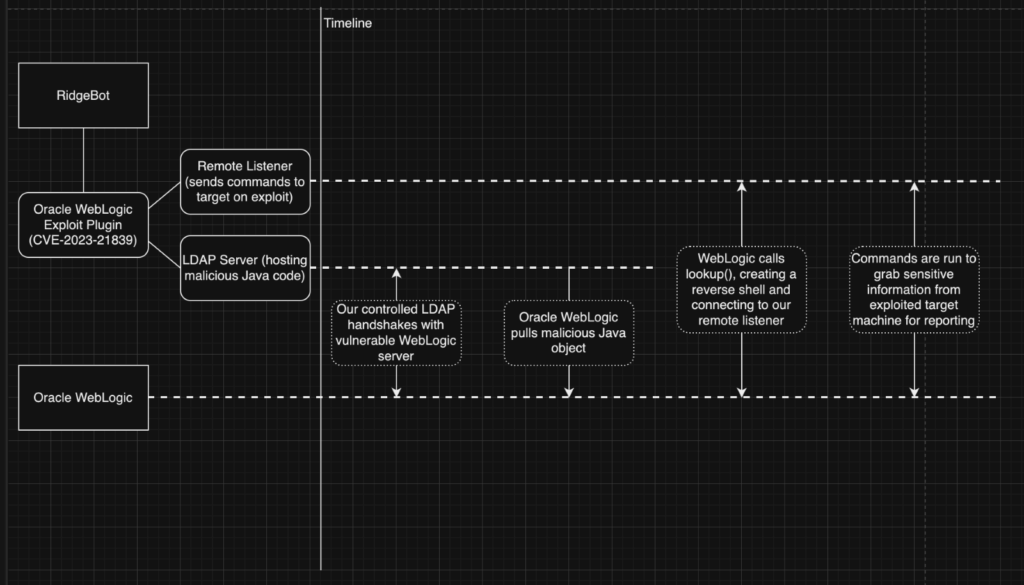
Figure 1: Timeline of how RidgeBot performs the exploit to gain control of Oracle WebLogic.
RidgeBot provides advanced automatic penetration testing to your organization. Vulnerabilities exist everywhere and it is paramount to be tireless in ensuring network security. By utilizing its extensive vulnerability library – which is constantly expanding – RidgeBot has an edge in detection, scanning, and ethical exploitation of dangerous vulnerabilities that could impact your business operations.
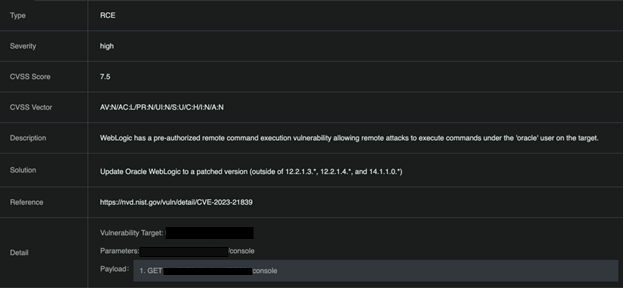
Figure 2: RidgeBot has fingerprinted a vulnerable instance of Oracle WebLogic.
RidgeBot can scan and exploit many potential weak points in an organization’s network. It is now equipped with the ability to scan and exploit this vulnerability in Oracle WebLogic and can provide detailed logs of how this vulnerability is exploited and where it lies in the organization. RidgeBot will automatically scan for vulnerable WebLogic instances running and will set up its own LDAP server and remote shell listener to safely perform the exploit found in CVE-2023-21839.
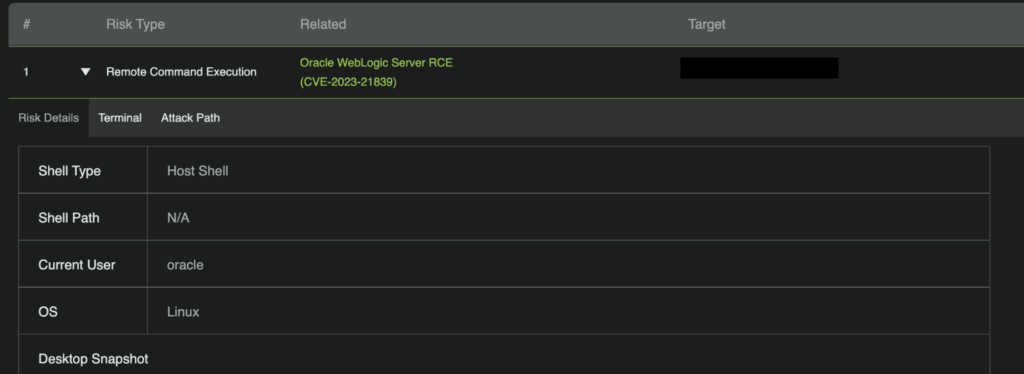
Figure 3: RidgeBot shows details about sensitive information gained from exploiting Oracle WebLogic.
RidgeBot shows you in real time what it is doing, what it has found, and the details it was able to collect about your vulnerable systems. In this case, it will give you details about the remote shell it was able to open on the target machine. This serves both to inform and to give proof about the exploitation and its potential dangers to a target network.
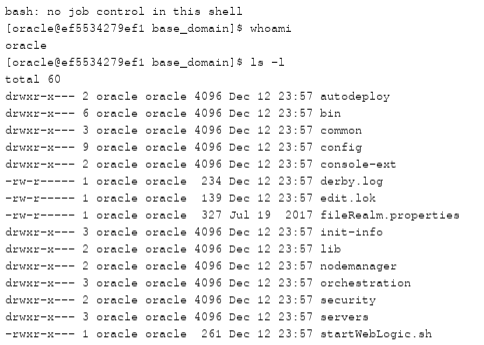
Figure 4: RidgeBot gives proof of exploitation. Here is a screengrab of some console commands RidgeBot has run on the exploited machine.
Make sure your organization is up to date and secure against potential cyber risks like this Oracle WebLogic vulnerability. To learn more about RidgeBot and what it can do for you, click here.
