Many exploit tools available today are only able to take one-step attack at a time. In order to achieve a multi-layered or iterative attack, Pen testers need to link the dots and command the system. Unlike these tools, RidgeBot, a fully automated penentration testing system, is able to dynamically perform multi-layered attacks without human’s interruption or command in between. The attack path is auto-planned based on knowledge the RidgeBot learned from the target. Let me show you an example.
In this exercise, my target is a MYSQL server. I’ll launch an attack toward it using RidgeBot. Let me first set it as my target in the Task template. As I know it’s a MYSQL server, I specifically choose exploit plugins relevant to MYSQL, and save it as a custom template. I choose the template and click “Run Now”…. And now I’m going to have a coffee and waiting for my result.
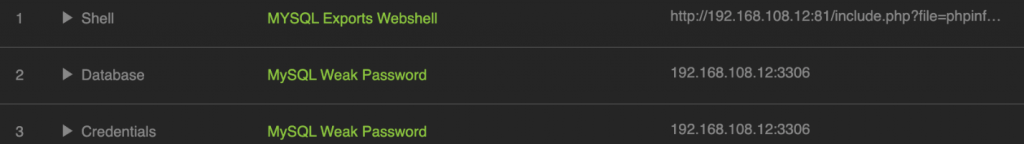
Here is it. After the test, we found three Vunlneralibilities. One MySQL week password, two MySQL exports webshell. These vulnerabilities generate 4 risk points. First is createntails crack, second is database information leakage, you can see here, all table displayed here. The other two risk points data type are shell. The RidgeBot could gain an access to the target’s webshell, and able to display the directory information. That means RidgeBot has a total control of this server. How did the RidgeBot get here?
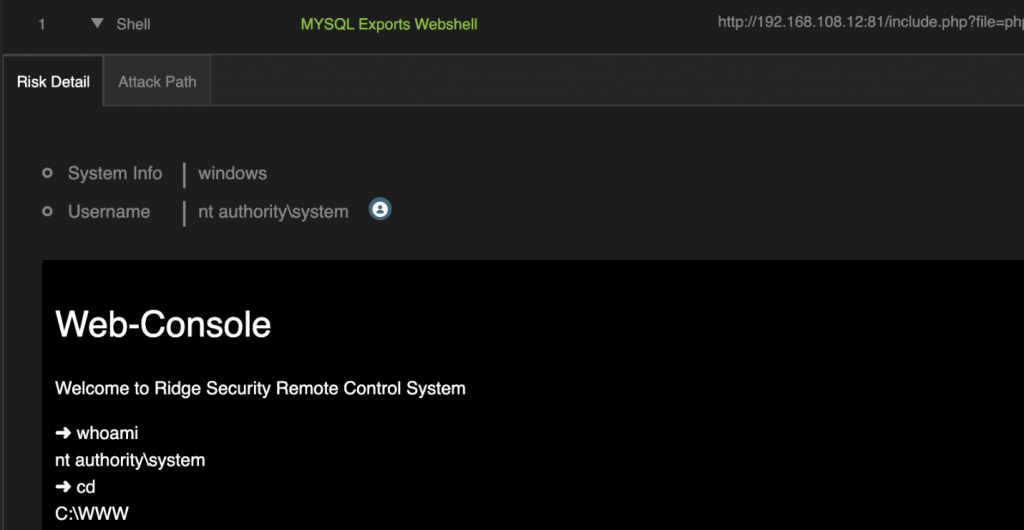
Let me explain what happened. In this exercise, the RidgeBot’s attack steps are:
Attack Path:
- Use Brute-Force to get the MySQL root password, if weak password is using.
- Try the weak password to get an access of MySQL.
- Use web poc to gain the web application directory info.
- Using MySQL outfile to implant a designed PHP payload into the web application directory.
- Mysql> select ‘<?php @eval($_POST[1]);?>’ into outfile ‘/www/bwapp/admin/phpinfo.php’
- When https://target.com/bwapp/admin/phpinfo.php get called, a persistent web-shell get created.
- Use web-shell, to gain the control
In this attack planing, there’re a few vulnerabilities exploited:
Vulnerabilities Exploited:
- MySQL weak password
- MySQL configuration to allow arbitrary file operation
- PHP webshell
- Sensitive info leakage such as the directory
As you can see, there is no stop and go during the attack. The RidgeBot made its own decision along the way based on new learning of the target’s weak password and finding of PHP based website, and it’s able to launch an appropriate attack such as an access with the weak password and injection of a php payload. This is what we called “fully automated”, which is a key differentiation of the RidgeBot from the tool in the market today.
And in the end, RidgeBot offered a remediation recommendation. For this target, the following shall be done to avoid any exploit from a real hacker.
Remediation
- Give strong password for MySQL root access.
- Upgrade MySQL >5.6.6 for strong password policy.
- Enable mysql file “write protection” in the configuration: configure secure_file_priv to the dedicated directory only.
- Have to validate all the PHP code with @eval.
Watch the demo here.
Have fun with RidgeBot!
