On April 22nd, Washington Post reported nearly 25,000 email addresses and passwords allegedly from NIH, WHO, Gates Foundation, and others, are dumped online.
According to a cybersecurity expert, 48 people from WHO have ‘password’ as their password. Others had used their own first names or change me.
The Weak Password as usual becomes an obvious entry point in this breach. Still many people haven’t realized, how easy the weak password could be disclosed. Let us show you an example with Ridge Bot, an automated security testing system.
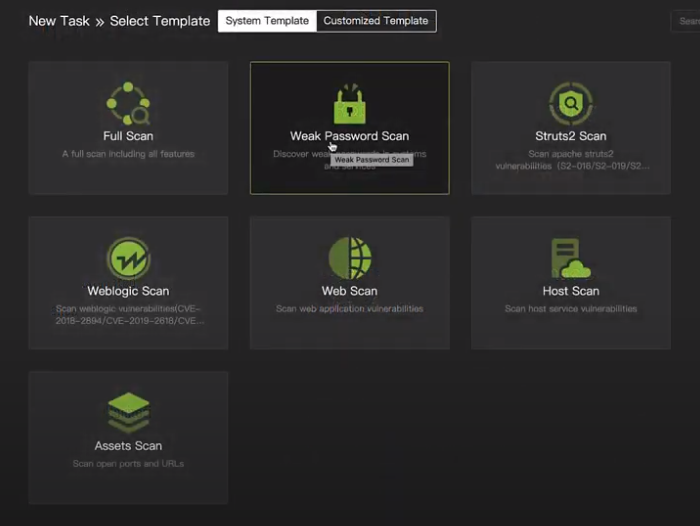
This is the graphic user interface of Ridge Bot system. We use a target Broken Web, published by OWASP for this test. First, let’s choose a template. There is even a standard template built in just for Weak Password. Select that, and then create a task. In the task, enter the IP address of the target web server. Then have it run. Just as simple as that.
The system first automatically discovers all attack surfaces including domains, URLs and login emails associated with this IP. Let’s see what it discovered.
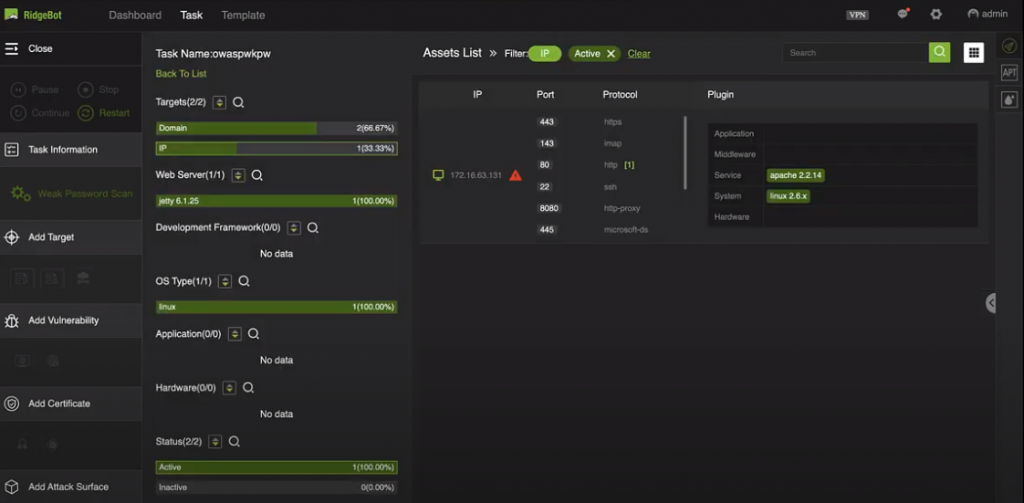
We found one “weak-password” instances. Click on first week password, here you are: account is root, password is admin. Using this account name and password, we can login to the web console.
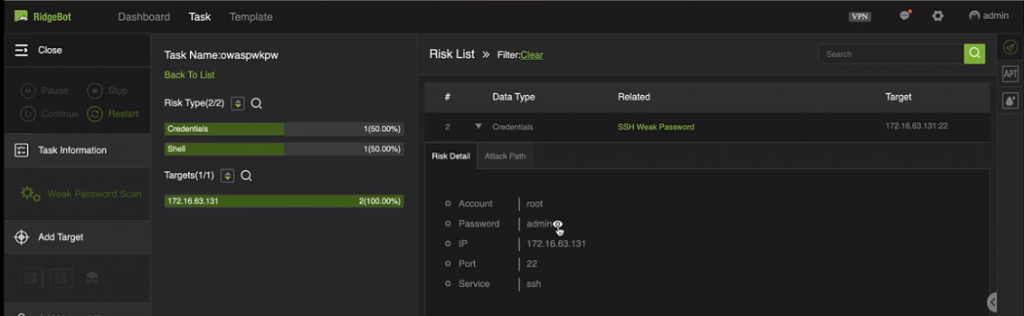
These commonly used weak passwords are stored into a dictionary built in the RidgeBot system. It’s an easy task for a computer to guess out.
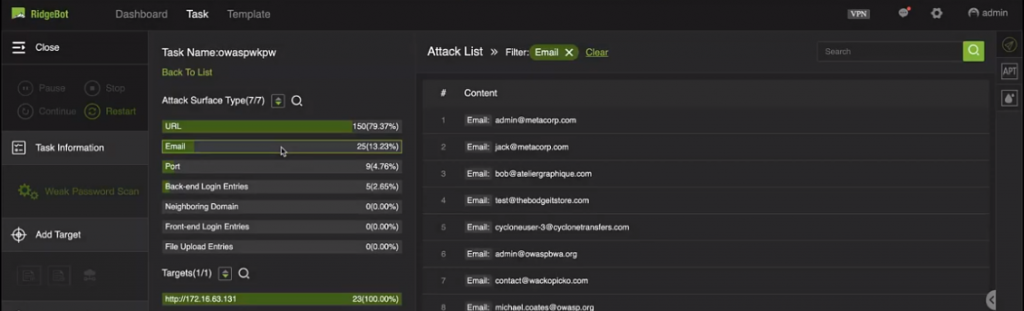
These emails we found through the earlier scanning, are user login names of this web site. You can imagine, by further guessing out these passwords, we can easily gain users’ account information.
Does this make you sweat?
End Covid-19, End Weak Passwords!
To learn more about RidgeBot, watch our demo now.
