Quite a few number of CISOs we talked to were puzzled about this: As a Fin-tech company, we’re relentless in keeping our apps secure. We use the best AST tools to examine our source code and make sure it’s flawless prior to its release. If my applications natively have no vulnerability, why do I need a penetration testing tool to prove it?
To answer this, we must first understand and compare two things: Application Security Testing (ATS) and penetration testing.
AST is designed to analyze application source code and test applications for security vulnerabilities. AST may use simulated attacks to assess and verify the security of the application. There are various AST technologies:
- SAST (Static AST):
- Dynamic (Dynamic AST)
- IAST (Interactive AST)
Let’s start with SAST. SAST focuses on inspecting the source code and identifies a flawed design at the code level. It requires in-depth understanding of each different programing language. However, it doesn’t cover the following issues that typically occur in a running environment or production stage:
- User mis-configuration (inappropriate filter setup; wrong authentication config, etc.)
- Weak passwords set by users
- Stolen credentials
- Parameters passed across different apps or front/back end systems
- Operating Systems
- Third party software in which no source code is available
In order to test/observe how an application behaves and processes users’ interactions in a running environment, you’ll need a DAST or/and IAST tool. The technology that an auto-pentest tool utilizes over a single application can be categorized as DAST or IAST.
DAST/IAST and Pentest (PT) share this commonality. However, PT itself has a much broader scope than just AST. Unlike AST, which stops at application testing, PT is designed to test against the overall IT infrastructure, including general applications, web applications, host servers and network devices, as well as end points, IoT and mobile devices, in some cases.
An auto-pentest tool such as RidgeBot™ assesses and identifies vulnerabilities not only within applications, but also within systems and networks. It delivers much wider coverage of IT assets and leverages more advanced hacking technologies. In addition to finding vulnerabilities to exploit, an advanced penetration test system leverages privilege escalation to make lateral movements from one application/system to another. This is the most effective way to test gaps between applications/systems, a critical feature that is not covered by an AST tool.
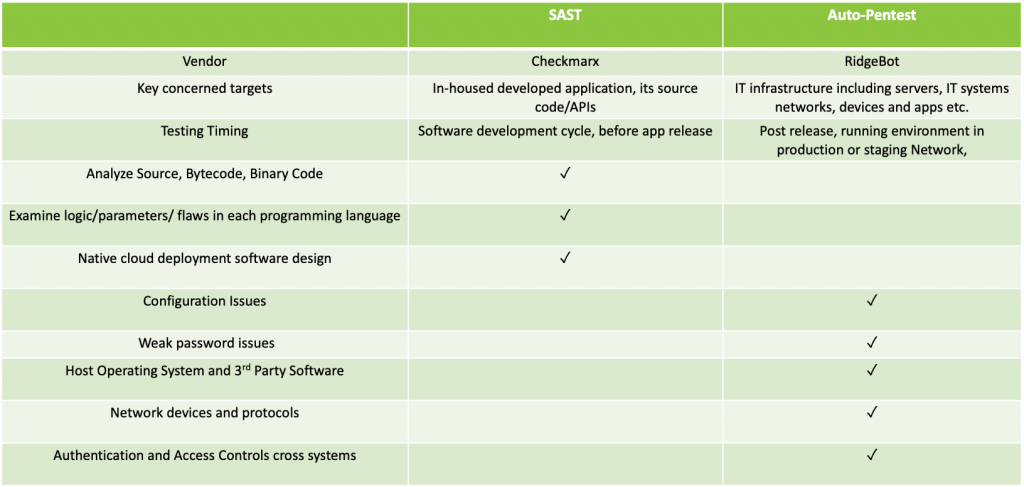
In summary, an auto-pentest doesn’t cover source code level examination that a tool like SAST does; rather they complement each other (See Table 1). An organization shall have both.
- SAST tool conducts the code level vulnerability examination on applications.
- Auto-pentests perform testing on applications in a running environment.
- Beyond applications, an auto-pentest tool covers systems, networks and any gaps in between applications, systems and networks.
For an organization with sufficient budget, they could have all these tools, SAST, DAST, IAST and PT. The coverage of each tool is simply illustrated in the following diagram:
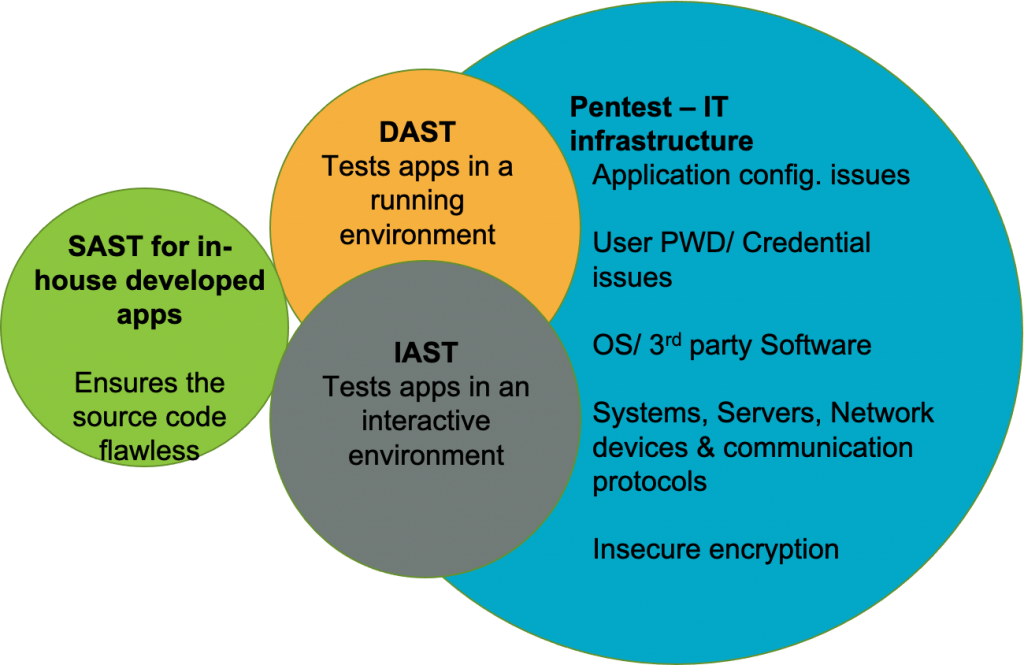
Table 1 SAST and Auto-Pentest Coverage Comparison