Fortra’s GoAnywhere MFT (Managed File Transfer) is a leading software solution favored by organizations. In addition to fulfilling the need for server-managed file transfer tasks, it provides multiple security features, such as end-to-end encryption and two-factor authentication. The software’s heavy focus on data security reflects the perpetually escalating challenges faced by organizations in today’s cyber environment.
The recent discovery of a critical vulnerability, CVE-2024-0204 – authentication bypass in Fortra’s GoAnywhere MFT before version 7.4.1, puts the data integrity and security of GoAnywhere MFT users at severe risk. With a staggering CVSS score of 9.8/10.0, this vulnerability allows network attackers to bypass authentication, create administrator accounts, and gain administrative privileges via remote exploitation. The heavy focus of GoAnywhere MFT on handling sensitive information and confidential files, combined with its other supported functionalities involving secret data, only magnifies the severity of this security vulnerability.
Given the critical nature and widespread implications of CVE-2024-0204, the research team at Ridge Security responded promptly. In particular, our researchers quickly identified the corresponding vulnerable attack surface exposed by GoAnywhere MFT, executed exhaustive penetration tests, and successfully exploited the vulnerability to gain administrator privileges on the target software deployed to our test server.
To protect the interests of organizations relying on GoAnywhere MFT, teams at Ridge Security rapidly developed plugins for RidgeBot – the AI-powered exposure management solution. The plugins, included as a part of the upgrade package released shortly after the revelation of CVE-2024-0204, benefit RidgeBot customers with the most up-to-date threat protection.
RidgeBot is equipped with a comprehensive suite of security scanning technologies to identify potential attack surfaces. With the latest release, RidgeBot customers can utilize the automatic penetration testing functionality of RidgeBot to detect CVE-2024-0204. Specifically, RidgeBot will scan the customer organization networks and use advanced fingerprinting technologies to identify GoAnywhere MFT instances vulnerable to the authentication bypass attack.
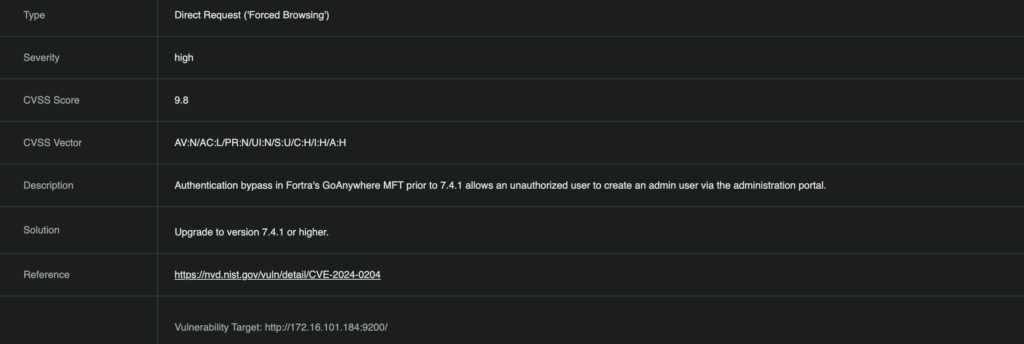
Figure 1: A vulnerable Fortra GoAnywhere MFT instance identified by RidgeBot via advanced fingerprinting
In addition to identifying potentially vulnerable instances, RidgeBot extends a step further to exploit the vulnerability benignly. Explicitly, RidgeBot will use specially crafted HTTP requests to circumvent the software’s authentication measures and create a new system administrator account. By logging into the software’s web portal with the RidgeBot-created account found in the penetration test report, customers can verify the success of exploitation by RidgeBot.
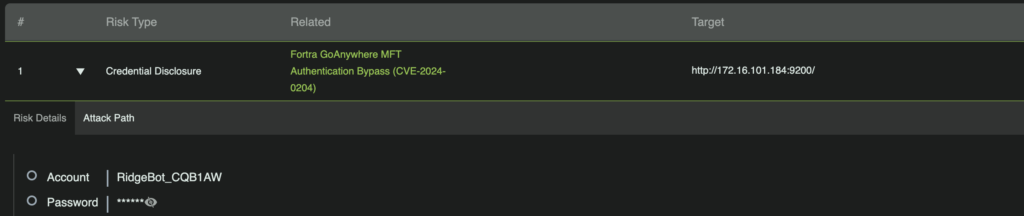
Figure 2: A new administrator account reported by RidgeBot as proof of a successful remote exploitation.
In a world with constantly emerging new digital threats, staying up to date is paramount. RidgeBot, with its expansive and ever-growing threat intelligence database, navigates you through the intricacies of the cybersecurity landscape. Get in touch with Ridge Security today to learn more about RidgeBot.
