RidgeBot Automated Pentesting Strengthens Security Across the DevSecOps SDLC
DevSecOps software supply chains have become a growing attack vector. Hence, software delivery pipelines and the tools used for building and deploying software need effective security tools that enable teams to use them on a regular basis, without friction.
DevSecOps teams need to rely upon automated user-friendly security tools that easily integrate into their processes to enable developers and operations personnel to work cohesively as they plan, build, and deploy code for production environments. DevSecOps agile development practices, cloud-native architectures, and open-source software require teams to use tools that support their continuous need for security and compliance throughout the software development lifecycle (SDLC).
Deploying automated pentesting within DevSecOps proactively discovers and validates any software vulnerabilities before bad actors find them. When pentesting becomes a priority from the very beginning of the planning process, it becomes an intuitive and natural function of the software development lifecycle.
Within a typical development process there can be many areas where vulnerabilities occur. Automated pentesting ethically exploits the vulnerabilities found, just as a hacker would in a real cyberattack. To ensure security is cohesively blended into DevSecOps, penetration testing should be performed on an ongoing basis to keep up with the continuous developments. Easy to use and intuitive automated pentesting allows developers to quickly identify flaws and vulnerabilities, while eliminating the time consuming and potential human error factor associated with manual testing.
RidgeBot strengthens DevSecOps security by finding and validating vulnerabilities
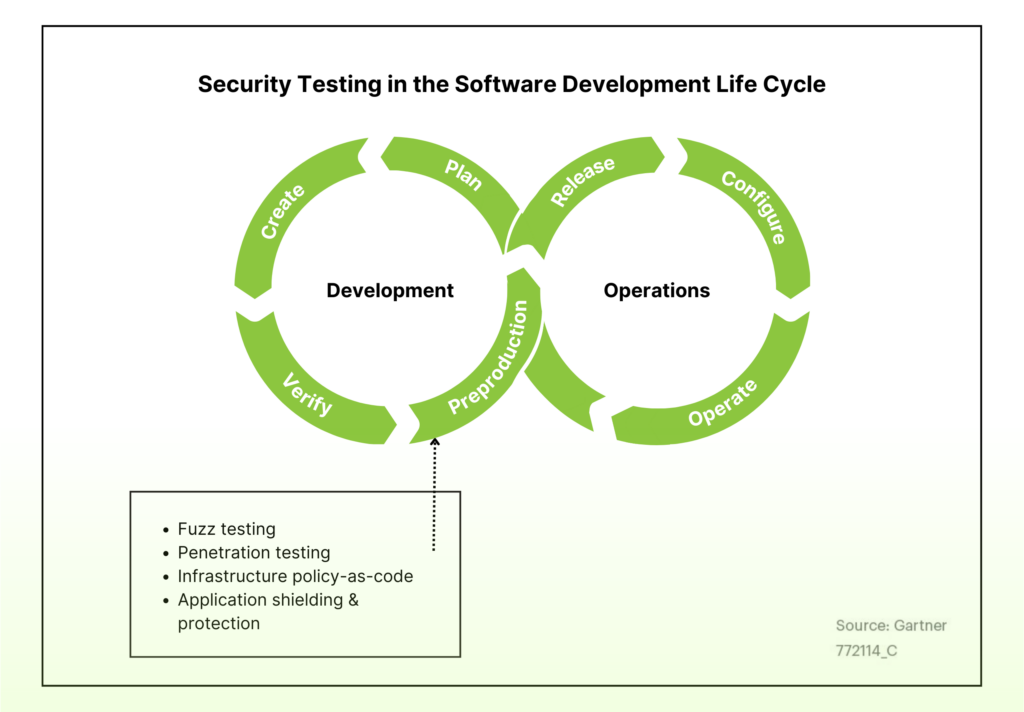
RidgeBot is an automated penetration testing system that enables DevSecOps to deliver secure software across the SDLC. Security must be embedded within the SDLC from planning, creation and verification, to preproduction, release, configuring and operation. RidgeBot reduces and helps remediate risks associated with attack surfaces through continuous risk assessment penetration testing. This is a critical component of a multi-layered DevSecOps security posture.
RidgeBot is easily deployed in the preproduction phase to ensure a secure development cycle. This provides the testing necessary to precisely model what would happen within a production environment. RidgeBot automates the entire attack process. When connected to a DevSecOps environment, it automatically discovers the assets and uses its collective knowledge database of vulnerabilities to mine the target system. Once RidgeBot discovers a vulnerability, it uses built-in ethical hacking techniques and exploit libraries to launch a real attack against the vulnerability. If successful, the vulnerability is validated and RidgeBot documents the entire kill chain transaction. Comprehensive reports include vulnerability, exploit, and attack surface details, as well as remediation advice and tools. This ensures the organization has the necessary security controls and defense mechanisms in place.
Early lifecycle deployment of RidgeBot enables DevSecOps with a strong security posture that reinforces every part of application and systems development, while reducing the possibility of data breaches. RidgeBot supports DevSecOps continuous closed loop of integrated security across their SDLC. RidgeBot can be integrated into an organization’s threat modeling to boost their security-by-design program. Embedded into the fast feedback capabilities, particularly within CI/CD environments, RidgeBot allows developers to quickly test as often as needed, and immediately respond to an automated feedback loop with reporting on any vulnerabilities found. This streamlines software development processes and review cycles, improving the security posture throughout the SDLC.
RidgeBot automated pentesting can be used after a significant change is made in a regulatory framework, such as when an application comes into the purview of the GDPR or PCI-DSS. Additionally, pentesting should be conducted after a new function or service is added that crosses a trust boundary, or after any modifications or additions to the production environment.
Conclusion
RidgeBot automated penetration testing predicts the potential losses suffered by an organization if the vulnerabilities found are exploited by the attackers. RidgeBot is easy and intuitive to use, which encourages developers to utilize pentesting on a regular basis. This supports the need for continuous development, while ensuring the code is tested and validated to be free from vulnerabilities.
Click here to learn more about how RidgeBot can protect your DevSecOps environment.
