In part one, we introduced “stealthier” Windows-based tools to detect MSSQL service: detect MSSQL instance based on the working group and detect MSSQL instance in a windows domain environment. In this blog, we share the Exploit of MSSQL, enable the target MSSQL xp_cmdshel, and enable the target MSSQL sp_oacreate.
Enable the target MSSQL xp_cmdshell
The Stored Procedure (SP) that begins with XP in MSSQL is an extended procedure. For example: xp_dirtree, XP_REGREAD, xp_subdirs, etc. xp_cmdshell can pass commands to cmd to execute. For security reasons, this feature is not open by default in MSSQL.
By default, only sysadmin or serveradmin has permission to run RECONFIGURE command. After the MSSQL version 2008r2, installed globally, no longer needs sysadmin or serveradmin permission, but instead requires low network permission to enable the extended procedure.
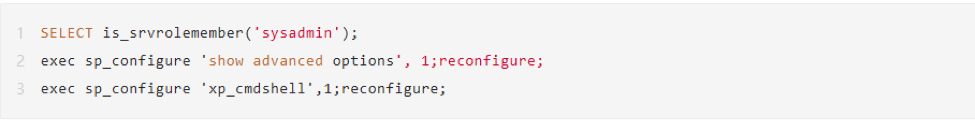
Example:
Try to remotely load the ps script to extract the clear text password in the host lsass memory procedure. Use the System.Text.Encoding class to convert the command to a Unicode byte array, and conduct utf_16_le encoding. After decoding, return to the target host to run. We did an actual test, and it’s evaded from anti-virus software.
Enable the target MSSQL sp_oacreate
If the dll file corresponding to the xp_cmdshell component in the target system is deleted or monitored by anti-virus software and returns to CreateProcess Error Code 5, we can still restore the sp_oacreate stored procedure to perform command execution sp_oacreate. The reference syntax is as follows:
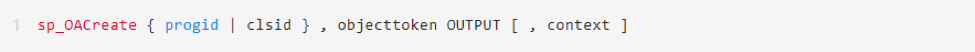
Progid is the programming identifier (ProgID) of the OLE object to be created. This string describes the class of the OLE object. Its format is OLEComponent, the component name of the OLE automation server. clsid is the class identifier (CLSID) of the object. This string describes the class of the OLE object, and its form is as follows:
‘{nnnnnnnn-nnnn-nnnn-nnnn-nnnnnnnnnnnn}’
Object is the name of the OLE object. The specified OLE object must be valid and must support the IDispLatLch interface. OUTPUT is the returned object tag, which must be a local variable of data type int. This object tag identifies the created OLE object and is used to call other OLE automated stored procedures. Use sysadmin permissions to enable OLE Automation Procedures configuration:
Example:
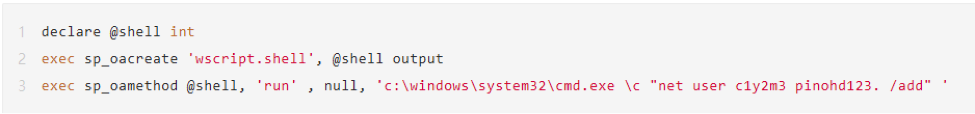
In this example, sp_oacreate creates the OLE object wscript.shell, which can also be other OLE objects. If no specific parameters are used, the NULL value is needed to pass as a placeholder when sp_oamethod calls the OLE object.
By calling sp_oacreate, we get a numeric return value 0 (success) or a non-zero number (failure), which is the return value of the OLE automation object. At the same time, commands cannot echo in this way. Of course, it is possible to obtain the corresponding command output using transmission protocols such as DNS and HTTP, but this is not the purpose at this time. Now that we can manipulate the COM object by using the sp_oacreate database stored procedure, we list the objects commonly used in OLE instances:
Scripting.FileSystemObject: Provides a set of file system operation functions
Scripting.Dictionary: Used to return a dictionary object storing key-value pairs
Wscript.Shell: Provides a set of functions for reading system information, such as reading and writing the registry, finding the path of the specified file, reading DOS environment variables, and reading the settings in the link
Wscript.NetWork: Provides functions for network connection and remote printer management. (Among them, all Scripting objects are stored in the SCRRUN.DLL file, and all Wscript objects are stored in the WSHOM.ocx file.)
The above are two examples of Exploit of MSSQL. Next time, we will share the method of implementing the command and obtaining the echo.
