Overview of RidgeBot®
Virtually eliminates false-positive vulnerabilities
Four ways to learn about RidgeBot®
Helpful Resources

RidgeBot® Report

RidgeBot® Whitepaper
RidgeBot® Online Demo
RidgeBot® Datasheet
Built for enterprise environments — works for any size business
Six Features Differentiate RidgeBot®
Smart Fingerprinting and Smart Web Crawling
RidgeBot® automatically crawls or scans the specified IT infrastructure to identify and document a broad type of assets and the attack surfaces of those assets
- 5600+ OS fingerprints/11000+ Service fingerprints
- Asset Types Supported: IPs, Domains, Hosts, OS, Apps, Websites, Plugins, Network and IoT Devices
The following technologies but not limited to are included in this stage:
- Crawling, URL brute force, domain name resolution, subdomain brute-force, associated domain extraction, neighboring site inspection, web fingerprint, host fingerprint, system fingerprint, active host inspection, email extraction, login entries discovery
Support all major web frameworks
- WordPress
- PHP/SQL
- VUE/React
- JavaScript
RidgeBrain Expert Model and Vulnerability Mining
By leveraging the Asset Profiling results, RidgeBot® will examine the assets and attack surfaces against its vulnerability knowledge base, discover all potential vulnerabilities to exploit:
- Web Applications
- Host/Database Servers
- Weak Credentials
- 3rd Party Framework vulnerabilities
The following techniques are used during the vulnerability mining process:
- Weakness discovering: Identify possible weak links on the attack surface and check for vulnerabilities based on the intelligent decision system such as the expert models and RidgeBot® brains.
- Vulnerability scanning: Access and test the target system by using packet generated by an automatic tool and the payload provided by the attack component, vector engine etc., and the returned results are checked to determine whether there are vulnerabilities that can be exploited.
Auto Exploitation
RidgeBot® has an extensive knowledge base, the customer can either choose the exploits based on the test goal and target; or choose to use full scan and have RidgeBot® conduct auto-exploitation.
- 2B+ threat intelligence
- 150K+ exploit database
- 6000+ build-in POC exploits
The following techniques are used during the vulnerability exploit process:
- Internal attack: Launch attacks from inside of Enterprise network with customer’s permission, focusing on exploiting vulnerabilities discovered on local network and systems.
- External attack: Launch attacks from outside Enterprise networks towards publicly accessible assets such as organizations’ websites, file shares, or services hosted in public cloud/CDN
- Lateral Movement: After gaining a permission to the target host, use the host as a pivot to further exploit vulnerabilities and gain access to other parts of the system.
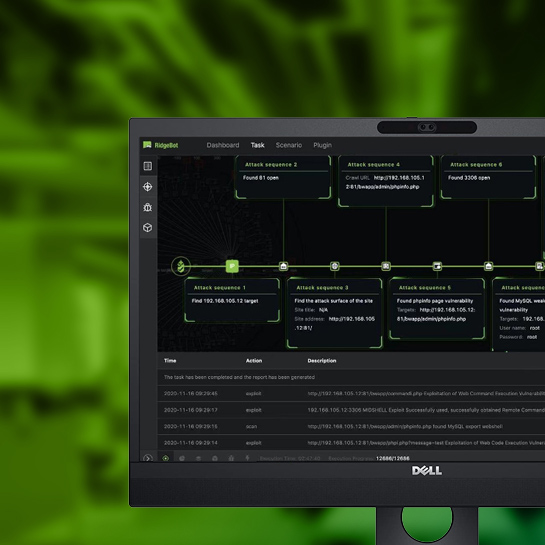
Realtime Attack Action Visualization
Auto Topology Drawing
- Shows relationships of assets and attack surfaces
- Map out vulnerabilities and risks
Full Attack Path Visibility
- Track the attack source and show the attack details
Show the real-time actions on the dashboard
- Discover
- Scan
- Exploit
Risk-based Assessment
Health Score: Rank and remediate vulnerabilities based on risk assessment
- Detailed and specific ranking of the most harmful vulnerabilities
- Visualize the kill-chain
- Comprehensive health score based on the weighted evaluation
Kill Chain Visualization: A Risk is defined as “An exploit with a completed kill-chain accomplished”
- Exploit attempts launched toward each exploitable vulnerability, only those accomplished the whole kill-chain will be documented in the final report.
- Four types of risks shown in the final report
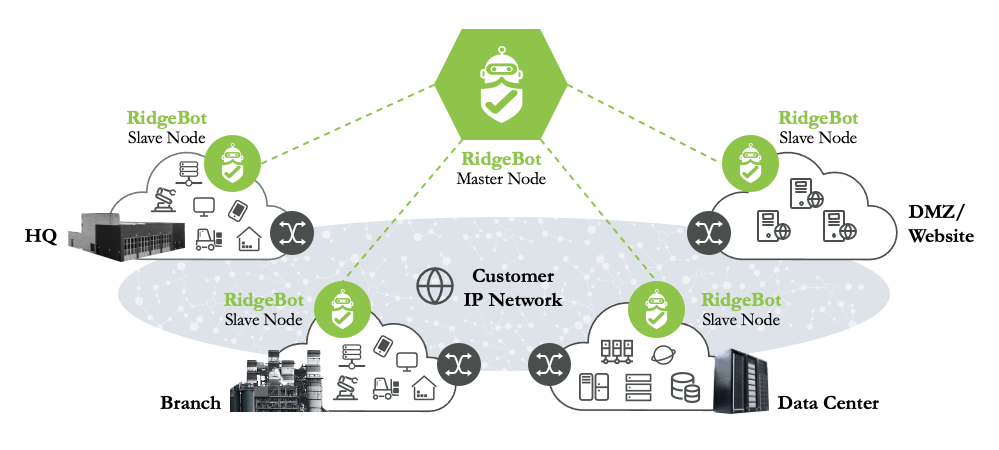
Distributed Architecture for Large Scale Infrastructure
Recommendation: One RidgeBot® Slave Node per 500 target systems (or per subnet)
- Smart Fingerprinting and Smart Web Crawling
- RidgeBrain Expert Model and Vulnerability Mining
- Auto Exploitation
- Realtime Attack Action Visualization
- Risk-based Assessment
- Distributed Architecture for Large Scale Infrastructure
RidgeBot® automatically crawls or scans the specified IT infrastructure to identify and document a broad type of assets and the attack surfaces of those assets
- 5600+ OS fingerprints/11000+ Service fingerprints
- Asset Types Supported: IPs, Domains, Hosts, OS, Apps, Websites, Plugins, Network and IoT Devices
The following technologies but not limited to are included in this stage:
- Crawling, URL brute force, domain name resolution, subdomain brute-force, associated domain extraction, neighboring site inspection, web fingerprint, host fingerprint, system fingerprint, active host inspection, email extraction, login entries discovery
Support all major web frameworks
- WordPress
- PHP/SQL
- VUE/React
- JavaScript
By leveraging the Asset Profiling results, RidgeBot® will examine the assets and attack surfaces against its vulnerability knowledge base, discover all potential vulnerabilities to exploit:
- Web Applications
- Host/Database Servers
- Weak Credentials
- 3rd Party Framework vulnerabilities
The following techniques are used during the vulnerability mining process:
- Weakness discovering: Identify possible weak links on the attack surface and check for vulnerabilities based on the intelligent decision system such as the expert models and RidgeBot® brains.
- Vulnerability scanning: Access and test the target system by using packet generated by an automatic tool and the payload provided by the attack component, vector engine etc., and the returned results are checked to determine whether there are vulnerabilities that can be exploited.
RidgeBot® has an extensive knowledge base, the customer can either choose the exploits based on the test goal and target; or choose to use full scan and have RidgeBot® conduct auto-exploitation.
- 2B+ threat intelligence
- 150K+ exploit database
- 6000+ build-in POC exploits
The following techniques are used during the vulnerability exploit process:
- Internal attack: Launch attacks from inside of Enterprise network with customer’s permission, focusing on exploiting vulnerabilities discovered on local network and systems.
- External attack: Launch attacks from outside Enterprise networks towards publicly accessible assets such as organizations’ websites, file shares, or services hosted in public cloud/CDN
- Lateral Movement: After gaining a permission to the target host, use the host as a pivot to further exploit vulnerabilities and gain access to other parts of the system.
Auto Topology Drawing
- Shows relationships of assets and attack surfaces
- Map out vulnerabilities and risks
Full Attack Path Visibility
- Track the attack source and show the attack details
Show the real-time actions on the dashboard
- Discover
- Scan
- Exploit
Health Score: Rank and remediate vulnerabilities based on risk assessment
- Detailed and specific ranking of the most harmful vulnerabilities
- Visualize the kill-chain
- Comprehensive health score based on the weighted evaluation
Kill Chain Visualization: A Risk is defined as “An exploit with a completed kill-chain accomplished”
- Exploit attempts launched toward each exploitable vulnerability, only those accomplished the whole kill-chain will be documented in the final report.
- Four types of risks shown in the final report
Recommendation: One RidgeBot® Slave Node per 500 target systems (or per subnet)
Reduce Time-to-Protection
RidgeBot’s® Pre-Defined Test Scenario Templates
Full Penetration
This test utilizes various network attack techniques used by hackers. Based on threat intelligence, exploit knowledge base, it profiles assets, mines vulnerabilities and launches attacks toward target assets. Attack targets: Any assets in Intranet, extranet or private network etc.
Ransomware
This test is packaged with several dozens of commonly used techniques seen in Ransomware attacks. It helps customers quickly validate if their environments are vulnerable to Ransomware attacks or not. And with a remediation plan suggested by the test, the customers can prevent themselves from the Ransomware attacks.
Website Penetration
This test launches cyber attacks against target websites, web applications and all related attack surfaces to gain control of the target website. The attack targets include self-developed or CMS based websites.
Internal Host Penetration
This test launches attacks from inside of corporate network to validate security system’s response toward an internal threat. It uses advanced techniques such as privilege escalation, lateral movement, domain penetration and others. The target of attack includes: all network accessible internal hosts.
Weak Credential Exploit
It launches direct or iterative attacks based on sensitive information collected via weak credential or unauthorized access vulnerabilities. Attack targets include: redis, elasticsearch, ActiveMQ, database, web login and other applications.
3rd Party Framework
It launches privilege escalation and iterative attacks based on known 1-day or n-day vulnerabilities detected onPenetration target the 3rd party framework. Attack targets include: Struts2, spring, fastjson, ThinkPHP and other frameworks.It launches privilege escalation and iterative attacks based on known 1-day or n-day vulnerabilities detected onPenetration target the 3rd party framework. Attack targets include: Struts2, spring, fastjson, ThinkPHP and ther frameworks.
Asset Profiling
This test profiles assets and digs out all attack surfaces based on domain names/sub-domain names, peripherals, encryption key, API, framework, open ports etc.
Request a demo with a particular scenario
View a sample RidgeBot business risk-based security report.
Registration
Please complete the form to view the recorded RidgeBot® demonstration.