Ready to protect your organization from rising ransomware attacks?
Don’t miss out on our exclusive White Paper
Take proactive measures in the face of challenges. In this document you’ll find:
- Ransomware attack statistics
- Trends fueling increased ransomware attacks
- State-of-the-art ransomware combat tactics
- How to harden your assets with Ridgebot
Discover the power of RidgeBot in combating ransomware!
RidgeBot’s approach covers two of the Top 3 ransomware infection vectors accounting for approximately 60% of incidents: Remote Desktop Protocol (RDP), and Software and Network vulnerabilities.
Download Report
Please complete the form to download the white paper.
Access our recommended mitigation actions
RidgeBot can help you determine which patches and upgrades are critical, and which ones are lower priority because they do not pose a realistic risk of exploitation.
Learn about techniques and operating modes
Ransomware authors and operators employ distinct categories: opportunistic and targeted. The latter can further be categorized into partnership and self-managed models.
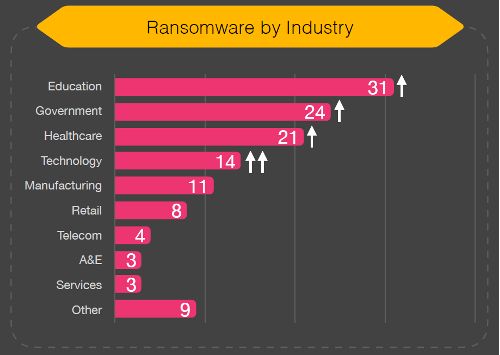
Education, Government and Healthcare are the industries most targeted by ransomware in 2023
BlackFog reports the following distribution.
The prospect of regulatory fines and reputation damage resulting from publicly exposed data privacy violations as well as government embarrassment and reputation damage significantly increase the success rate and size of payouts.
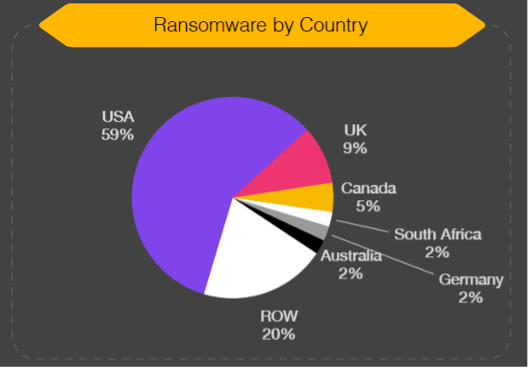
Ransomware attacks primarily target North America and Europe
BlackFog reports the following country distribution.
It is essential to emphasize that no country or organization is immune to these threats, highlighting the critical need for enhanced cybersecurity measures worldwide. Vigilance and proactive defense are imperative to safeguard against such attacks.
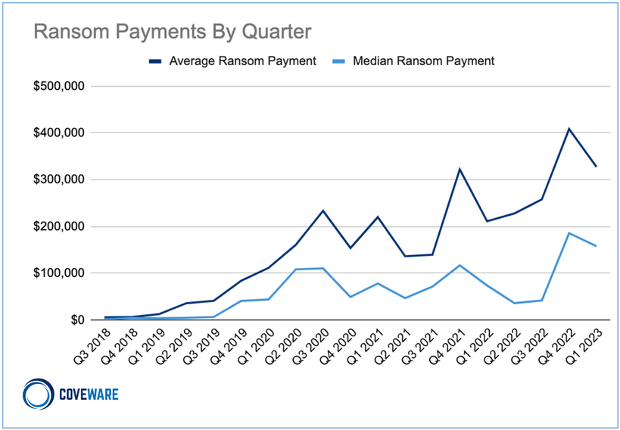
The average ransom payout is inexorably upwards
It is, in part, attributed to cyber attackers deliberately targeting larger companies and institutions. These entities often possess more significant financial resources, making them potentially lucrative targets for ransomware operators.
Deploy Ridge Security’s RidgeBot
RidgeBot contains critical scan and exploit capabilities specifically developed to combat vulnerabilities leading to targeted ransomware attacks. Learn how RidgeBot can help your organization survive these dangerous times.
Please complete the form to download the Ransomware white paper.
