On May 27, 2023, CISA cybersecurity advisory announced that a previously unknown SQL injection vulnerability (CVE-2023-34362) was exploited in Progress Software’s managed file transfer software, MOVEit Transfer.
Progress Software’s MOVEit vulnerability impacts on-premises and cloud-based versions of its file-transfer service. The actively exploited SQL injection vulnerability allows threat actors to escalate privileges and gain unauthorized access to customer environments.
This same year, Sutter Health in Northern California informed customers of a breach that may have impacted their sensitive, personally identifiable, and protected health information. On July 26, 2023, Sutter Health was alerted to a compromise of their MOVEit Transfer server related to publicly known software vulnerabilities.
Shortly after, on August 11, 2023, the Colorado Department of Health Care Policy and Financing (HCPF) notified more than 4 million individuals, that their personal healthcare data was exposed in the MOVEit breach. The files contained their full names, Social Security numbers, Medicaid and Medicare ID numbers, birth dates, home addresses, demographic and income information, clinical and medical information, and health insurance information.
The MOVEit vulnerability is a serious threat to the healthcare sector, as it can compromise the confidentiality, integrity, and availability of the data, which are the three pillars of cybersecurity. The breach can also have severe consequences for patients, such as identity theft, fraud, blackmail, and even physical harm.
Average Data Breach Cost In Healthcare Sector
Individuals Affected
Corporates Affected
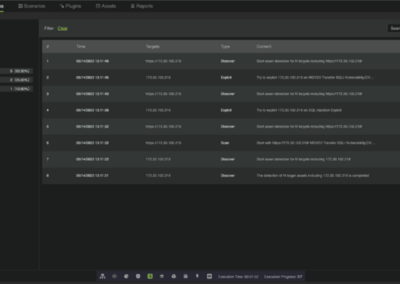
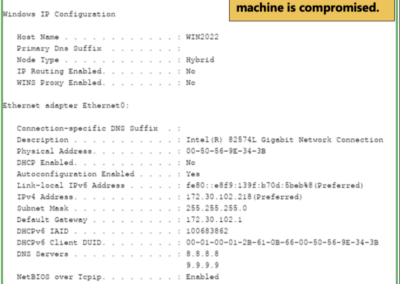
RidgeBot® addresses a broad spectrum of cybersecurity exposures across an organization’s digital environment, and our plugin library now includes CVE-2023-34362. The screenshots below show RidgeBot® discovering the MOVEit vulnerability, its attack logs, and evidence of the MOVEit Exploit.
RidgeBot® automated pentesting eradicates the threat of CVE exposures like MOVEit
Staying ahead of potential threats constantly challenges security teams in the ever-evolving cybersecurity landscape. Even the most fortified systems can have vulnerabilities that malicious actors exploit. The risk is amplified within critical industries like healthcare. This is where opportunistic cyber criminals, such as the CI0P ransomware gang, demonstrate their innovative techniques through their creation of the MOVEit hack.
RidgeBot® automated penetration testing is a crucial ally for all organizations, enabling them to uncover weaknesses, vulnerabilities, and exposures lurking within their digital assets. RidgeBot® automated pentesting drastically narrows the timeframes for hackers to seize opportunities – compressing them from months to hours. This is achieved by running tests when network configurations change, new applications are released, or user groups are allocated.
Ridge Security is in the business of outsmarting cybercrime
At the heart of Ridge Security’s RidgeBot® automated penetration testing lies collective threat intelligence, vulnerability insights, and AI-powered decision-making. Armed with cutting-edge security validation methodologies, RidgeBot® simulates the actions of a genuine attacker. Unyielding in its pursuit, it identifies, exploits, and meticulously documents its findings.
RidgeBot® discovers attack vectors, validates vulnerabilities, and provides actionable recommendations for remediation, all before hackers capitalize on them. RidgeBot’s continuous, automated testing empowers defenders to proactively fortify the security fabric across every facet of their digital domain. And it’s easy to use without requiring highly skilled personnel.
Act Now and Elevate Your Cybersecurity with RidgeBot®

RidgeBot’s Support for OpenSSH Server RCE Vulnerability CVE-2024-6387 Detection
OpenSSH is the premier connectivity tool for remote login with the SSH protocol. It provides a large suite of secure tunneling capabilities, several authentication methods, and sophisticated configuration options. It is the default SSH implementation in most UNIX and...
New RidgeBot Release: Balancing Automation and Control
There are many similarities between viruses and malware - they both can mutate and become more resilient at each variation. From a health perspective, we seek stronger, more targeted remedies. From a cybersecurity perspective, this means that security vendors need to...