
by Ridge Security Marketing | Apr 30, 2020 | Pen Test Technical Tips
In part one, we introduced “stealthier” Windows-based tools to detect MSSQL service: detect MSSQL instance based on the working group and detect MSSQL instance in a windows domain environment. In this blog, we share the Exploit of MSSQL, enable the target...

by Ridge Security Marketing | Apr 20, 2020 | AI in Automated Pen Test
CAPTCHAs—Completely Automated Public Turing test to tell Computers and Humans Apart. To train a computer or “robot” to become an ethical hacker is not a trivial task. The obvious question that comes to mind is, “how can it pass CAPTCHAs—automated...

by Ridge Security Marketing | Apr 20, 2020 | Pen Test Technical Tips
In penetration testing, we often encounter an MSSQL database. Usually, we will use an extended procedure like xp_cmdshell to perform privilege escalation or execute system commands. However, when xp_cmdshell is unused, what other methods can we leverage? We are...
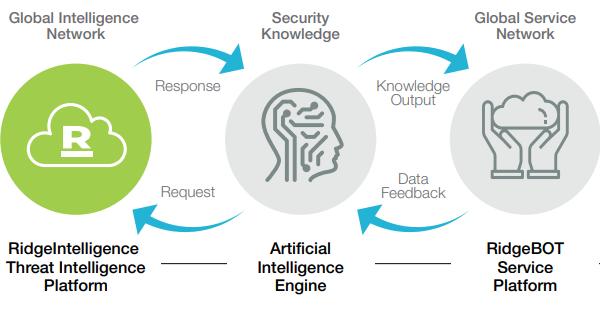
by Ridge Security Marketing | Apr 13, 2020 | RidgeBot
Ridge Security is transforming Security Validation with RidgeBot, an Intelligent Security Validation Robot. RidgeBot’s are modeled using techniques utilized by literally millions of hackers that penetrate systems. When...

by Ridge Security Marketing | Apr 8, 2020 | Blog
White Hat Hackers can help your company stay on the offensive against cyber attackers, and save your data and money. https://bit.ly/39cgJsl#pentesting #whitehat Source: builtin.com





